Netstat for Security Professionals – Cybersecurity Leadership
Netstat for Security Professionals
In the ever-evolving landscape of cybersecurity, vigilance is paramount. Security professionals rely on a diverse toolkit to monitor, detect, and respond to threats.
Among these indispensable tools, the netstat command stands out as a fundamental utility for gaining immediate insight into the network connections traversing a system.
This article delves into the various facets of the netstat command, demonstrating how its capabilities can be leveraged to scrutinize network activity, identify suspicious connections, and enhance overall security posture.
Understanding netstat: Your Window into Network Activity
At its core, netstat (network statistics) is a command-line utility that displays network connections (both incoming and outgoing), routing tables, and a number of network interface statistics. For security professionals, it acts as an essential diagnostic tool to quickly ascertain the state of network communications on a host.
Let’s explore the most critical netstat parameters and their applications:
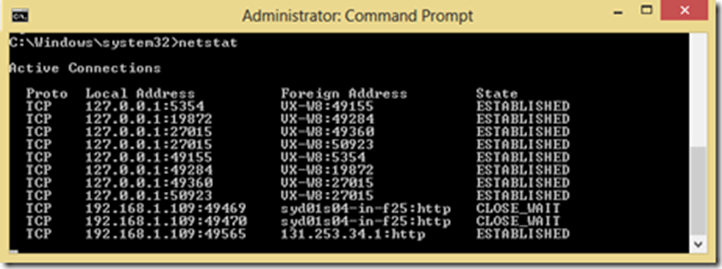
netstat : Displays the status of active TCP and UDP ports. This basic command provides a snapshot of currently established connections.


Netstat –a : Display All Connections and Listening Ports.
This command is crucial for comprehensive network auditing. It reveals all active connections and, more importantly, all ports that the system is currently listening on. Security professionals can use this to identify unauthorized services or potential backdoors that might be listening for incoming connections.


netstat –b: Display Executable Involved in Connections.
This powerful option displays the name of the executable program responsible for creating each connection or listening port. This is invaluable for pinpointing suspicious processes. If an unfamiliar application is making outbound connections or listening on a port, netstat -b can quickly identify its source.
netstat –e: netstat -e: Display Ethernet Statistics.
This parameter provides statistics about the network interface, such as the number of bytes and packets sent and received. While not directly showing connections, it offers a high-level view of network traffic. It can be combined with -s for more detailed protocol statistics:
netstat -f: Display Fully Qualified Domain Names (FQDN).
Instead of just showing IP addresses, this option resolves foreign addresses to their fully qualified domain names. This can provide more context about the remote hosts your system is communicating with, making it easier to identify legitimate versus potentially suspicious domains.
netstat -n: Display Numerical Addresses and Port Numbers.
This command displays active TCP connections, but addresses and port numbers are expressed numerically without attempting to determine hostnames. For security professionals, -n is highly valuable during incident response as it provides immediate results without the delay of DNS lookups, which can be critical when time is of the essence.
netstat -o: Display Process ID (PID) for Each Connection. This option displays active TCP connections and includes the process ID (PID) for each connection. The PID is a vital piece of information as it allows you to cross-reference the connection with a specific process in the Windows Task Manager (or equivalent process manager on other OS). This parameter can be combined with -a, -n, and -p for more detailed analysis:
netstat -ano (A highly recommended command for security professionals, showing all connections, their PIDs, and numerical addresses).
netstat –r: Displays the contents of the IP routing table. (This is equivalent to the route print command under Windows.)
netstat –s: Displays statistics by protocol. By default, statistics are shown for the TCP, UDP, ICMP, and IP protocols
netstat –v: When used in conjunction with -b it will display the sequence of components involved in creating the connection or listening port for all executables
netstat -r: Display IP Routing Table. This command displays the contents of the IP routing table, which dictates how network traffic is routed from your system. While less about active connections, it’s crucial for understanding network paths and identifying potential route manipulations or misconfigurations. (This is equivalent to the route print command on Windows).
netstat -s: Display Statistics by Protocol. This option displays statistics for various protocols, including TCP, UDP, ICMP, and IP. It provides insights into network traffic patterns and potential anomalies within specific protocols.
netstat -v: Display Sequence of Components (Verbose). When used in conjunction with -b, this option displays the sequence of components involved in creating the connection or listening port for all executables. This provides a more granular view into the underlying modules and libraries.
Common Combinations for Security Analysis:
netstat -ano: Shows all connections, their numerical addresses, and the associated Process ID. This is an extremely powerful command for identifying the applications behind network activity.
netstat -na: Displays all connections and listening ports numerically.
Conclusion
The netstat command is an indispensable tool in the arsenal of any security professional. Its ability to quickly reveal active connections, listening ports, and the processes behind them provides immediate visibility into the network state of a system. By mastering its various options, you can effectively monitor for unauthorized activity, troubleshoot network issues, and contribute significantly to maintaining a robust security posture. Regular use of netstat empowers you to be proactive in detecting and responding to potential threats on your network.
netstat Parameters
| Parameter | Description |
|---|---|
| -a | Displays all active TCP connections and the TCP and UDP ports on which the computer is listening. |
| -b | Displays the executable involved in creating each connection or listening port. In some cases well-known executables host multiple independent components, and in these cases the sequence of components involved in creating the connection or listening port is displayed. In this case the executable name is in [] at the bottom, on top is the component it called, and so forth until TCP/IP was reached. Note that this option can be time-consuming and will fail unless you have sufficient permissions. |
| -e | Displays Ethernet statistics, such as the number of bytes and packets sent and received. This parameter can be combined with -s. |
| -n | Displays active TCP connections, however, addresses and port numbers are expressed numerically and no attempt is made to determine names. |
| -o | Displays active TCP connections and includes the process ID (PID) for each connection. You can find the application based on the PID on the Processes tab in Windows Task Manager. This parameter can be combined with -a, -n, and -p. |
-p |
Shows connections for the protocol specified by Protocol. In this case, the Protocol can be tcp, udp, tcpv6, or udpv6. If this parameter is used with -s to display statistics by protocol, Protocol can be tcp, udp, icmp, ip, tcpv6, udpv6, icmpv6, or ipv6. |
| -s | Displays statistics by protocol. By default, statistics are shown for the TCP, UDP, ICMP, and IP protocols. If the IPv6 protocol is installed, statistics are shown for the TCP over IPv6, UDP over IPv6, ICMPv6, and IPv6 protocols. The -p parameter can be used to specify a set of protocols. |
| -r | Displays the contents of the IP routing table. This is equivalent to the route print command. |
|
Redisplays the selected information every interval seconds. Press CTRL+C to stop the redisplay. If this parameter is omitted, this command prints the selected information only once. |
| /? | Displays help at the command prompt. |
| Parameter | Description |
|---|---|
| Proto | The name of the protocol (TCP or UDP). |
| Local address | The IP address of the local computer and the port number being used. The name of the local computer that corresponds to the IP address and the name of the port is shown unless the -n parameter is specified. If the port is not yet established, the port number is shown as an asterisk (*). |
| Foreign address | The IP address and port number of the remote computer to which the socket is connected. The names that corresponds to the IP address and the port are shown unless the -n parameter is specified. If the port is not yet established, the port number is shown as an asterisk (*). |
| State | Indicates the state of a TCP connection, including:CLOSE_WAITCLOSEDESTABLISHEDFIN_WAIT_1FIN_WAIT_2LAST_ACKLISTENSYN_RECEIVEDSYN_SENDTIMED_WAIT |
Some examples :
- netstat -e -s
- netstat -s -p tcp udp
- netstat -o 5
- netstat -n -o
Keywords
Essential Components of a Zero Trust Architecture : Free VIDE0
Microsoft netstat
linux networking commands is netstat netstat for incident response command is used to check