-
PHISHING
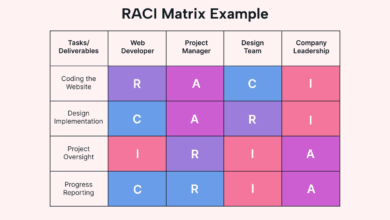
NIST 800-53 Compliance Checklist and Security Controls Guide
Ensuring compliance with NIST SP 800-53 is critical for aligning your cybersecurity efforts with federal standards. This popular cybersecurity framework…
Read More » -
WEB ATTACK

The Ultimate Guide to Creating a Cybersecurity Incident Response Plan
Date: 5 August 2025 Have you read our recent monthly compilations of the biggest cyber attacks in 2025? If you…
Read More » -
CLOUD

The Ultimate PC Builder’s Toolkit: Top 10 Essential Tools
Building your own PC can be a rewarding experience, allowing you to customize every aspect of your machine to meet…
Read More » -
WEB ATTACK
-
CLOUD

Easily Assign Relevant Training With Our Training Planner
Keeping your IT security awareness training continuous and relevant doesn’t have to be time consuming. With our training planner, you…
Read More » -
EXPLOITS

How to get fast board buy-in for your cyber security project — Matt Palmer
To experts, the business case for cyber security change programmes can seem clear as day — it can be hard…
Read More » -
EXPLOITS

How AI Will Redefine the 12 Cybersecurity Platforms
Hello Cyber Builders 🖖 We’re back at it—diving deeper into the world of cybersecurity platforms that are shaping the future.…
Read More » -
JACKING

Preventing Zero-Click AI Threats: Insights from EchoLeak
EchoLeak (CVE-2025-32711) is a recently discovered vulnerability in Microsoft 365 Copilot, made more nefarious by its zero-click nature, meaning it…
Read More » -
PHISHING

How Dealerships Can Protect Their Customers’ Financial Data
Dealerships handle sensitive information, such as credit applications and personal financial records, daily. A data breach can lead to profound…
Read More » -
WEB ATTACK

Core Writing Word and Page Counts
I want to make a note of the numbers of words and pages in my core security writings. The Tao…
Read More »