-
INSIDER

CIO Imperatives: Dr. Timothy C. Summers on Digital Trust, AI, and Why a Trusted CISO is Non-Negotiable 1
CIO Imperatives: Dr. Timothy C. Summers on Digital Trust, AI, and Why a Trusted CISO is Non-Negotiable In an era…
Read More » -
JACKING

Meet This Year’s Europe Community Meeting Keynote Speaker, Bernie Collins
This episode of Coffee with the Council is brought to you by our podcast sponsor, Feroot. Welcome to our…
Read More » -
PHISHING
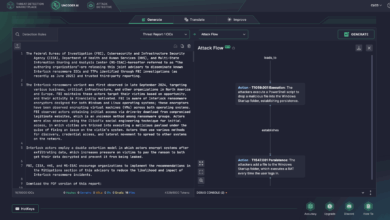
Interlock Ransomware Detection: The FBI, CISA, and Partners Issue Joint Alert on Massive Attacks via the ClickFix Social Engineering Technique
In mid-July 2025, researchers spread the news of the reemergence of the Interlock ransomware group, leveraging a modified version of…
Read More » -
SPYWARE

MDR Services Benefits and Best Practices
Cybersecurity today demands more than basic defenses. Firewalls, antivirus software, and traditional intrusion prevention systems can no longer stop determined…
Read More » -
WEB ATTACK
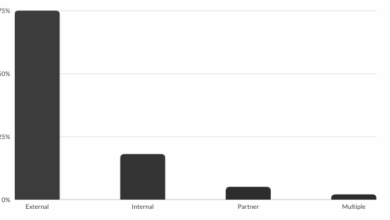
2023 Breaches and Incidents: Personal Notes
Introduction In today’s digital landscape, the prevalence of cyber threats and incidents has become a significant concern for individuals, organizations,…
Read More » -
CLOUD

WinRAR zero-day exploited in espionage attacks against high-value targets
The attacks used spearphishing campaigns to target financial, manufacturing, defense, and logistics companies in Europe and Canada, ESET research finds…
Read More » -
EXPLOITS

Quantum-ready data security: Safeguarding information beyond binary
Abstract In the rapidly advancing landscape of quantum computing, the potential for revolutionary processing power also brings forth significant challenges…
Read More » -
INSIDER

Black, White and Gray Box
Editor’s note: On the example of network security, Uladzislau describes the essence, pros and cons of black, gray, and white box…
Read More » -
JACKING

Heimdal® Achieves Fifth Consecutive ISAE 3000 SOC 2 Type II Certification
COPENHAGEN, Denmark, July 23, 2025 – Heimdal is proud to announce that it has once again secured the ISAE 3000…
Read More » -
PHISHING
Using Exposed Ollama APIs to Find DeepSeek Models
The explosion of AI has led to the creation of tools that make it more accessible, leading to more adoption…
Read More »