-
INSIDER
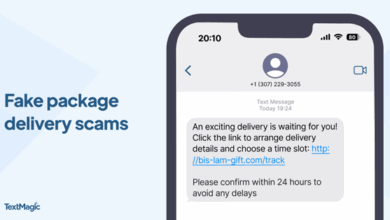
Mobile security matters: Protecting your phone from text scams
It all starts so innocently. You get a text saying “Your package couldn’t be delivered. Click here to reschedule.” Little do…
Read More » -
PHISHING

Becky Holmes Knows Who *Isn’t* Dating Keanu Reeves
Becky Holmes loves DMing with scammers. When it comes to romance scammers, she will do whatever it takes, pursuing them…
Read More » -
SPYWARE

Top 6 VAPT Tools for 2024 You Should Know
IntroductionCybersecurity threats continue to evolve, making Vulnerability Assessment and Penetration Testing (VAPT) an essential practice for organizations. In this blog,…
Read More » -
WEB ATTACK
Digital Privacy Risks During Family Breakdowns
Date: 13 August 2025 After a family breaks up or a relationship ends, digital privacy becomes more important but is…
Read More » -
CLOUD

Using AWS ACM with xrdp on Ubuntu ~ Since We Can Export Certs Now | by Teri Radichel | Cloud Security | Jul, 2025
Well, AI helped a little but I had to do a lot myself and it took WAY. TOO. LONG. ~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~…
Read More » -
EXPLOITS

Why Nation-States Are Hacking the Power That Runs the World
“If you want to weaken a nation without firing a shot, start by flipping the switch.” Hello Cyber Builders 🖖,…
Read More » -
PHISHING

OnlyFans DMCA Takedown – How To Handle Copyright Removals As A Creator
In this post, I will show you how to handle copyright removals as a creator for an OnlyFans DMCA Takedown.…
Read More » -
SPYWARE
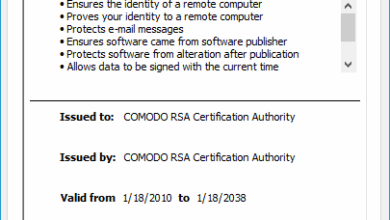
Comodo RSA Certification Authority: Trusted Root CA Explained
The COMODO RSA Certification Authority is one of the most widely distributed root CAs in the world. Its certificates form…
Read More » -
WEB ATTACK

-
EXPLOITS

A Journey to the Highest Cybersecurity Maturity: Compliance, Part 8 | by Vicente Aceituno Canal
Compliance Management Press enter or click to view image in full size Photo by Anne Nygård on Unsplash Previously in…
Read More »