-
INSIDER

What Is a Data Breach and How to Prevent It?
Let’s be honest: few phrases can make your stomach drop faster than “your data has been compromised.” Whether you’re an…
Read More » -
PHISHING

Empowering The Soc: Stop Detecting Potential Threats, Start Signaling Real Attacks
The cybersecurity landscape is constantly evolving, and security operations centers (SOCs) are feeling the pressure to stay ahead of increasingly…
Read More » -
SPYWARE

What is XMPP ❓ — Extensible Messaging & Presence Protocol | by Ivan Novikov
Introduction In the early 2000s, when the idea of chat applications was shaping, XMPP was allowing developers to construct interactive…
Read More » -
WEB ATTACK
Who Owns CMMC Evidence Collection in a Small Business?
The Cybersecurity Maturity Model Certification, CMMC, is a critical part of ensuring robust and equal information security from top to…
Read More » -
CLOUD

Weekly Update 464
I think the most amusing comment I had during this live stream was one to the effect of expecting me…
Read More » -
EXPLOITS

Unveiling the Secrets of the Dark Web
Introduction The internet, often regarded as a vast and mysterious realm. It is not a singular entity but rather a…
Read More » -
INSIDER

Fortnite Impersonation Scams: A No-Nonsense Parent Guide
Even years after its release, Fortnite still stands as the online “battle royale” game of choice, with millions of younger…
Read More » -
PHISHING

How OAuth and device code flows get abused
Microsoft Entra ID, the identity backbone of Microsoft’s cloud ecosystem, is increasingly targeted through techniques like Device Code Phishing and…
Read More » -
WEB ATTACK
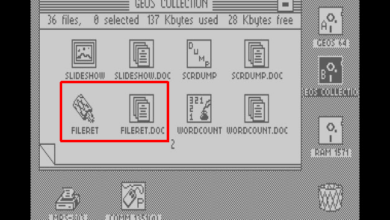
Retrieving Deleted Files on the Commodore C64 in 1987
When I was a sophomore in high school, from 1987 to 1988, my friend Paul and I had Commodore C64…
Read More » -
CLOUD

How the always-on generation can level up their cybersecurity game
Digital natives are comfortable with technology, but may be more exposed to online scams and other threats than they think…
Read More »