-
PHISHING
![Is OnlyFans Safe? [Here’s The ANSWER] 🙂 Is OnlyFans Safe? [Here’s The ANSWER] 🙂](https://blogflarehost.com/wp-content/uploads/2025/08/OnlyFans-Overview-390x220.jpg)
Is OnlyFans Safe? [Here’s The ANSWER] 🙂
Is OnlyFans Safe? Read on to find out in this post. Remote working platforms like Zoom and engaging social networks…
Read More » -
SPYWARE

Server side template injection — SSTI vulnerability ⚠️ | by Ivan Novikov
Introduction There is hardly any software development or other linked elements that haven’t fallen into the trap of cyber vulnerabilities.…
Read More » -
WEB ATTACK

Elder Fraud Victims Lose Millions Each Year
Elder Fraud Victims Lose Millions Each Year – How to Protect Yourself and Your Loved Ones
Read More » -
CLOUD

Check your risk blind spot
Does your business truly understand its dependencies, and how to mitigate the risks posed by an attack on them? 12…
Read More » -
EXPLOITS

What is a Data Subject Access Request (DSAR) – Data Privacy Manager
When the General Data Protection Regulation (GDPR) was enforced back in 2018, it was set out to give individuals control…
Read More » -
INSIDER

Key Concepts in Digital Forensics & Cybersecurity
Cyberattacks don’t just hit networks. They hit trust. And once that’s gone, the road to recovery can be long and…
Read More » -
JACKING

The Impact of Security Breaches on Educational Institutions
This blog was originally published by Bravura here. Educational institutions oversee hundreds or thousands of students and faculty members…
Read More » -
PHISHING
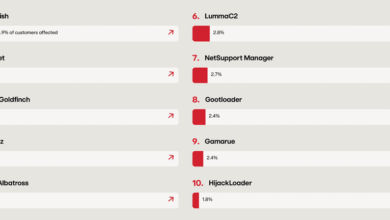
A Deep Dive into Impacket Remote Code Execution Tools
IMPACKET OVERVIEW Impacket was originally developed as a toolkit for penetration testing, providing security professionals with powerful capabilities to simulate…
Read More » -
WEB ATTACK
FedRAMP vs StateRAMP Cost Comparison Guide
Cloud service providers looking to work with the government, whether it’s at the state and local level or at the…
Read More » -
CLOUD

Unlocking Cybersecurity Success: Navigating Careers with Certifications
Navigating a Successful Career Transition in Cybersecurity: The Crucial Role of Certifications In the fast-paced and competitive field of cybersecurity,…
Read More »