-
PHISHING
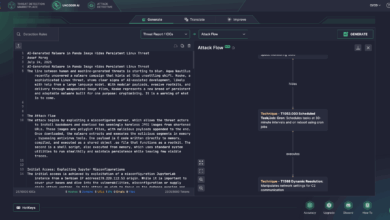
Koske Malware Detection: New AI-Generated Linux Threat in the Wild
Attackers are increasingly leveraging AI to compromise critical business assets, signaling a dangerous evolution in the threat landscape. Check Point…
Read More » -
SPYWARE

The Role of EDR in Real-Time Threat Detection & Response
Understanding how EDRs work requires examining the sophisticated mechanisms that enable these systems to detect, analyze, and respond to cybersecurity…
Read More » -
CLOUD

How to handle and spot phishing mails with Microsoft Defender
In the previous blog post, we went through how Microsoft Defender can strengthen your email security. If you haven’t read…
Read More » -
EXPLOITS

Why We Must Embrace Risk and Learn From Incidents — Matt Palmer
Welcome to Incidentally: Why We Must Embrace Risk and Learn From Incidents As humans, we don’t take risks just for…
Read More » -
INSIDER
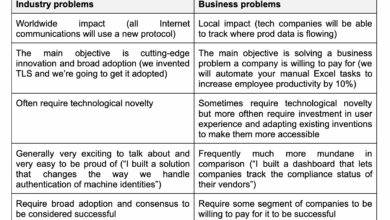
In security, not every industry problem is a business problem
Nobody can deny that there are many problems in our field. Just attend an industry conference or speak with five…
Read More » -
JACKING
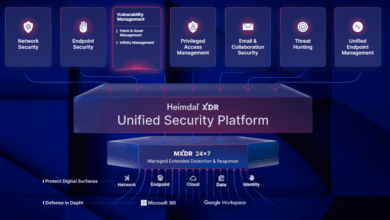
Attack Surface Management Software: Top 10 Vendors
Key Takeaways: What is attack surface management? Why is attack surface management important? What are the best ASM vendors? Over…
Read More » -
SPYWARE
Google’s Strongest Security for Mobile Devices
Posted by Il-Sung Lee, Group Product Manager, Android Security Protecting users who need heightened security has been a long-standing commitment…
Read More » -
EXPLOITS

What Is Your Digital Footprint Revealing to Attackers—and How Can You Turn It into a Defense?
Your online presence—social media posts, web registrations, breach data—creates a digital footprint that attackers can study and exploit without you…
Read More » -
INSIDER

Thank You for a Remarkable Cyber Security & Cloud Expo Global!
The remarkable Cyber Security & Cloud Expo Global has concluded its highly anticipated two-day event at Olympia London on…
Read More » -
JACKING
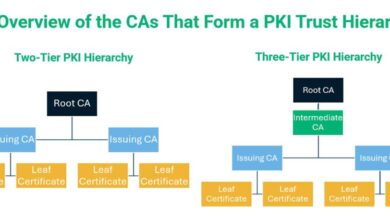
Demystifying PKI Technology: An Essential Guide for IT Security Professionals
Learn everything you need to know about PKI technology in IT security that enables organizations to establish trust in a…
Read More »