-
EXPLOITS

A Journey to the Highest Cybersecurity Maturity: Quality, Part 10
Quality Management Continue reading on The CISO Den »
Read More » -
Ransomware Tops Growing Cyber Threats in Healthcare, Driving Up Breach Costs
ScienceSoft, a US-based healthcare IT consulting company with over 20 years of experience in cybersecurity, released a non-sponsored study exploring…
Read More » -
PHISHING

Beth Should Have Dated the IT Guy
Beth sent more than $26,000 to a man she met on Tinder. It was a romance scam, but one that…
Read More » -
SPYWARE
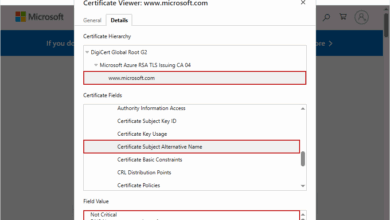
What is a SAN SSL Certificate?
If an organization handles multiple number of domains, subdomains, or internal services, it is likely to become inefficient or error-prone.…
Read More » -
WEB ATTACK
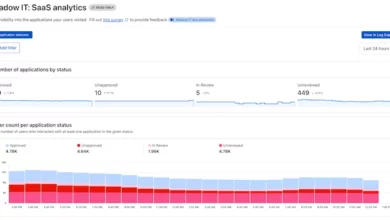
Cloudflare secures sensitive data without fully restricting AI usage
Cloudflare announced new capabilities for Cloudflare One, its zero trust platform, designed to help organizations securely adopt, build and deploy…
Read More » -
CLOUD
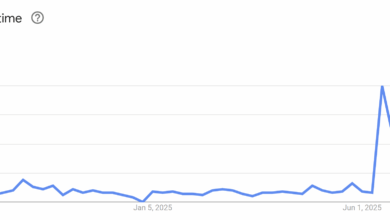
That 16 Billion Password Story (AKA “Data Troll”)
Spoiler: I have data from the story in the title of this post, it’s mostly what I expected it to…
Read More » -
EXPLOITS
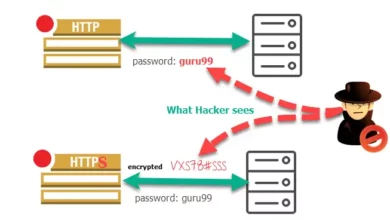
SSL Pinning Bypass with Frida and effective Mitigation techniques
Introduction In an era of unprecedented digital transformation, securing sensitive data and communications has never been more critical. One of…
Read More » -
INSIDER
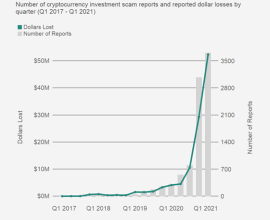
Strategies to overcome the cryptocurrency scam
Cryptocurrency has revolutionized financial transactions, offering speed, anonymity, and decentralization. However, the rise of cryptoscams has become a significant concern…
Read More » -
JACKING

Revisiting UNC3886 Tactics to Defend Against Present Risk
On July 18, Singapore’s Coordinating Minister for National Security K. Shanmugam revealed that the country was facing a highly sophisticated…
Read More » -
PHISHING

Why More People Are Using Document Generators?
Here, I will discuss how to get proof of address instantly. Also, I will reveal why more people are using…
Read More »