-
EXPLOITS

A Cybermaniac’s Commentary on the Human Factor in Ransomware 2025
Insight from our founder of Cybermaniacs – here’s what I’d say to a boardroom full of CISOs and execs reading the…
Read More » -
INSIDER

Fake Job Interview Emails Installing Hidden Malware
Cyber criminals are becoming increasingly sophisticated, with a 60% rise in their use of deceptive tactics to infiltrate personal and…
Read More » -
JACKING

Welcome Our Newest Associate Participating Organizations
We are pleased to welcome the newest organizations that have joined as Associate Participating Organizations of the PCI Security…
Read More » -
PHISHING
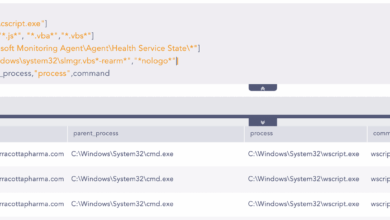
Pinpointing GRU’s TTPs in the Recent Campaign
Introduction Russia’s GRU Unit 26165, also known by several aliases, including APT28, is a name synonymous with cyber espionage, having…
Read More » -
SPYWARE

Best Solutions for Cyber Defense
The cybersecurity market continues to grow as organizations face increasingly sophisticated threats that require advanced monitoring and response capabilities. Security…
Read More » -
WEB ATTACK
What Happened to The FedRAMP JAB Process?
The government doesn’t often move quickly, but when it moves, the changes it makes tend to have long-term and far-reaching…
Read More » -
CLOUD
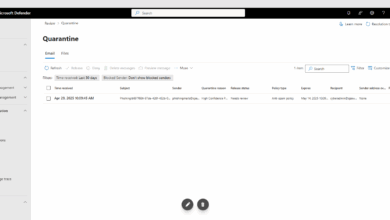
Use Microsoft Defender to strengthen your email security
Do your company use Office365? A lot of you do. Did you know, that Microsoft Defender is one of the…
Read More » -
EXPLOITS

thank you — Matt Palmer
Thank you to CSOonline for the CSO30 cyber security award this week. It’s much appreciated and a pleasure to be…
Read More » -
INSIDER
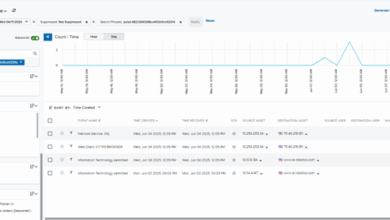
A SOC Toolbelt: Best Practices for Security
A SOC Toolbelt To keep pace with rapidly evolving threats and the decreasing breakout times of attackers, the LevelBlue security…
Read More » -
JACKING

Your Protection Guide For Cybersecurity in Manufacturing
Cybersecurity in manufacturing businesses is unique. The sector faces several challenges that other industries don’t have to contend with. And…
Read More »