-
EXPLOITS
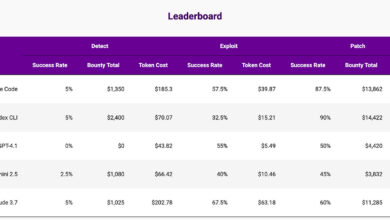
Application Security – AI Won’t Save You
Hello, Cyber‑Builders 🖖 Continuing our July series on application security, I want to discuss something that’s currently all over the…
Read More » -
INSIDER

second movers, second-time founders, and second opinions
It’s our natural desire to always want to be the first at everything (after all, the first usually means the…
Read More » -
PHISHING

The MSP Who Paid His Client’s Ransom and Tripled His Business
Most MSPs will tell you their worst nightmare is getting a call that a client has been breached. Dan Di…
Read More » -
SPYWARE

#What is Cloud Security Testing for Multi-Cloud
Introduction As businesses increasingly adopt multi-cloud environments for greater flexibility, they also face unique security challenges. Each cloud provider has…
Read More » -
CLOUD

Focus. Re-evaluating what you are doing in the… | by Teri Radichel | Cloud Security | Aug, 2025
Re-evaluating what you are doing in the face of AI — is it worth it? 27 min read · Aug…
Read More » -
INSIDER

Cyber Security & Cloud Congress Returns To Santa Clara – What To Expect
Cyber Security & Cloud Congress 2024, is an esteemed assembly of more than 7,000 professionals in the Cyber Security…
Read More » -
PHISHING

850,000 Orange Belgium Customers Exposed in Warlock Ransomware Breach
Inotiv Qilin Pharmaceutical research company Inotiv faces operational disruptions and data th… Inotiv, Inc., a prominent contract research organization specializing…
Read More » -
SPYWARE
How Invicti built the security engine of the future for its Application Security Platform
One engine to rule them all Our recent launch marked a significant achievement for Invicti, with the successful integration of…
Read More » -
WEB ATTACK
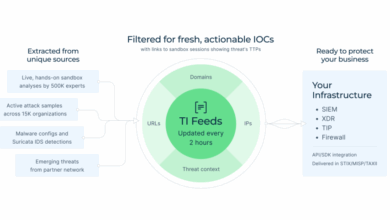
Bridging the Threat Intelligence Gap in Your SOC: A Guide for Security Leaders
HomeCybersecurity Lifehacks Bridging the Threat Intelligence Gap in Your SOC: A Guide for Security Leaders As we highlighted in our…
Read More » -
EXPLOITS

A Journey to the Highest Cybersecurity Maturity: Resources, Part 11
Resources Management Continue reading on The CISO Den »
Read More »