-
INSIDER
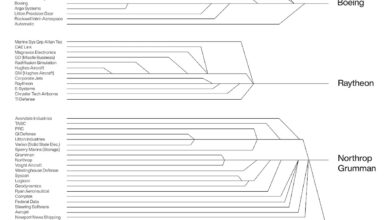
how 200 companies became 11
I am attending Black Hat this week, and in many conversations I’ve had so far, one theme keeps coming up:…
Read More » -
PHISHING
The Cybersecurity Risks of Unmanaged Internet-Facing Assets
Because unmanaged assets are not continuously monitored for security risks, they likely contain cybersecurity exposures, like software vulnerabilities and cloud…
Read More » -
SPYWARE
What’s the Difference and Which One Do You Need?
Phishing is outpacing defenses, and inboxes are flooded with lookalike senders. Hence, visual trust has become a frontline necessity and…
Read More » -
WEB ATTACK
ANY.RUN & OpenCTI: Transform SOC for Maximum Performance
HomeIntegrations & connectors ANY.RUN & OpenCTI: Transform SOC for Maximum Performance Editor’s note: The current article was originally published on…
Read More » -
CLOUD

Allianz Life hit by hackers, customer and staff personal data stolen • Graham Cluley
US insurance firm Allianz Life has told the media that hackers stole personal info of the “majority” of its customers…
Read More » -
EXPLOITS

CISO, how do you measure maturity? | by Vicente Aceituno Canal | The CISO Den
No, is not how you thought Press enter or click to view image in full size ISMS maturity is not…
Read More » -
INSIDER

5 Reasons to Attend Cyber Security & Cloud Congress North America 2024
Explore the forefront of enterprise technology at the Cyber Security & Cloud Congress North America. Delve into the entirety…
Read More » -
JACKING

New Ransomware Charon Uses Earth Baxia APT Techniques to Target Enterprises
The malware attempts to drop this driver as %SystemRoot%\System32\Drivers\WWC.sys and register it as the “WWC” service. However, our analysis revealed…
Read More » -
PHISHING

Agent Fatigue Crisis Hits 89% of MSPs as Security Tools Backfire
COPENHAGEN, Denmark – August 11, 2025 – Security tools meant to protect managed service providers are instead overwhelming them. A…
Read More » -
SPYWARE

What is threat modeling ❓ Definition, Methods, Example | by Ivan Novikov
Threat modeling is a method for upgrading the security of an application, system, or business process by distinguishing objections and…
Read More »