-
EXPLOITS

Indicators of Compromise in Threat Intelligence: Real-Time Action
Organizations face mounting pressure from cyber threats that exploit detection delays. Industry data shows breach costs averaging $4.45 million per…
Read More » -
INSIDER

Smart Home Data Breach Exposes 2.7 Billion Records
Mars Hydro, a Chinese company that makes IoT devices like LED lights and hydroponics equipment, recently suffered a massive data…
Read More » -
JACKING
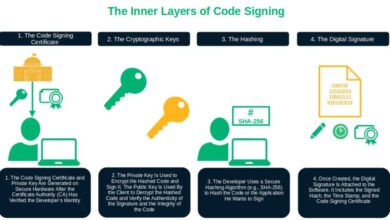
5 Real-World Software Nightmares That Code Integrity Verification Could Have Prevented
Learn from the past to prepare for the future with these 5 infamous cyber attacks (and their disastrous consequences) that…
Read More » -
PHISHING

Make Phishing Training Count with HootPhish
Stop tricking employees. Start training them. Take Control of Your Security Awareness Training with a Platform That’s as Effective as…
Read More » -
SPYWARE

Why Application Detection and Response (ADR) is Essential for Security
Introduction: In an age where digital transformation is at the core of every business, securing applications has become crucial. While…
Read More » -
WEB ATTACK

BLACK HAT FIRESIDE CHAT: Straiker extends ‘red teaming’ to the AI layer as AI attacks surge
The enterprise software model that defined the past two decades — SaaS — is being rapidly eclipsed by a new…
Read More » -
CLOUD

Hospital fined after patient data found in street food wrappers • Graham Cluley
I’m a big fan of recycling. But what about recycling our private data? Like medical records? Well, according to local…
Read More » -
EXPLOITS
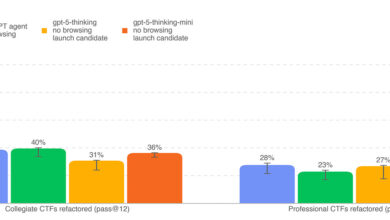
GPT-5 Is Around the Corner. Stop Treating AI Like a Threat—Hire It.
Hello Cyber Builders 🖖, Every time a new AI model drops, the same debate starts: Is it safe? Could it…
Read More » -
INSIDER

What is an insider threat, and how to identify it
In 2024, the average cost of an insider threat incident reached $17.4 million.[1] When you consider that these types of…
Read More » -
PHISHING
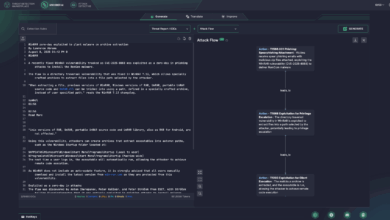
CVE-2025-8088 Detection: WinRAR Zero-Day Is Actively Exploited in the Wild to Install RomCom Malware
Update: This article has been updated to reflect ESET research insights from August 11, 2025, covering the emerging attack flow…
Read More »