-
PHISHING

What to Expect in 2025
2024 is coming to a close, and with it a banner year for cybercrime. Megabreaches that would have grabbed front-page…
Read More » -
SPYWARE
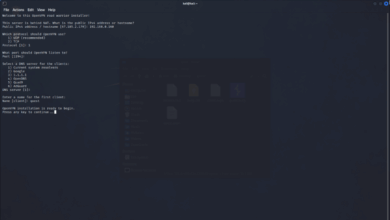
Setting Up a Pentesting Environment for the Meta Quest 2
With the advent of commercially available virtual reality headsets, such as the Meta Quest, the integration of virtual and augmented…
Read More » -
CLOUD

AI can be vaccinated against evil, and the “Rumble in the Silicon Jungle” • Graham Cluley
In episode 64 of The AI Fix, AI discovers new physics, a robot crab looks for love on the beaches…
Read More » -
EXPLOITS

when you don’t respond to a crisis — Matt Palmer
A few years ago I wrote a short article about the Titanic, and the lessons for cyber risk management. However,…
Read More » -
INSIDER

India’s First Global Computer Virus
In the cinematic tapestry of cybersecurity, where tales of intrigue and innovation collide, one story emerges from the shadows of…
Read More » -
SPYWARE
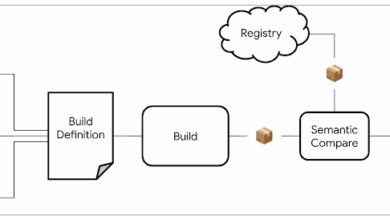
Open Source, Rebuilt to Last
Today we’re excited to announce OSS Rebuild, a new project to strengthen trust in open source package ecosystems by reproducing…
Read More » -
WEB ATTACK
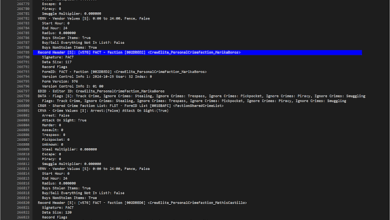
Creating a Large Text File Viewer by Vibe Coding with Visual Studio Code, Cline, OpenRouter, and Claude 3.7
The problem I was trying to solve this time was opening and searching extremely large text files. I…
Read More » -
CLOUD

How to mine millions without paying the bill • Graham Cluley
In episode 431 of the “Smashing Security” podcast, a self-proclaimed crypto-influencer calling himself CP3O thought he had found a shortcut…
Read More » -
EXPLOITS

How Behavioral Analysis Drives Fast Reactions in Today’s SOCs
The field of cybersecurity changes , and Security Operations Centers (SOCs) need to leave behind old signature-focused tools. SOCs now…
Read More » -
INSIDER

Why your computer will thank you for choosing Webroot Essentials
Let’s be honest – nobody wants antivirus software that slows down their computer. You know the feeling: you install security…
Read More »