-
JACKING

Fortinet VPNs Under Coordinated Attack
Time for your Weekly Cyber Snapshot with Adam Pilton, former Cybercrime Investigator, currently Cybersecurity Advisor.The five major cyber stories this…
Read More » -
SPYWARE
The Role of Wireless Intrusion Detection: Guard Against Invisible Threats
Guarding Against Invisible Threats: The Role of Wireless Intrusion Detection Wireless connectivity is foundational to modern business. From corporate offices…
Read More » -
WEB ATTACK

News alert: Link11 warns of rising API and bot attacks, launches integrated WAAP platform
Frankfurt, Germany, Aug. 20, 2025, CyberNewswire — Link11, a Germany-based global IT security provider, has released insights into the evolving…
Read More » -
CLOUD
Europol says Telegram post about 50,000 Qilin ransomware award is fake
It’s not unusual for law enforcement agencies to offer substantial rewards for information which might lead to the identification, arrest,…
Read More » -
EXPLOITS

Not a Magic Wand, But a Multiplier
Hello Cyber Builders 🖖 This week, I’m announcing a new series on Intelligent Security. That’s the name we used at…
Read More » -
INSIDER

Biggest-Ever Crypto Heist: $1.5B Stolen from Bybit
In a stunning development shaking the digital asset world, cyber criminals executed the largest crypto heist ever recorded by siphoning…
Read More » -
JACKING
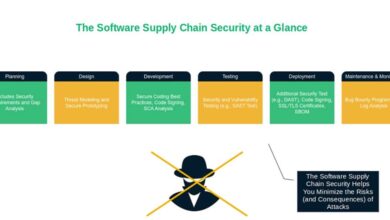
The Ultimate Guide to Software Supply Chain Security Risks, Threats, and Mitigations
In July 2025, a core node package manager (npm) package with 28+ million downloads per week was compromised, exposing millions…
Read More » -
PHISHING
CyberHoot Newsletter – June 2025
CyberHoot June Newsletter: Stay Informed, Stay Secure Welcome to the June edition of CyberHoot’s newsletter, where we keep you up…
Read More » -
SPYWARE

SAST vs. DAST: Choosing the Right Approach for Application Security
Introduction With the increasing complexity of web applications and the rise in sophisticated cyber threats, implementing a robust security testing…
Read More » -
CLOUD

Weekly Update 466
I'm fascinated by the unwillingness of organisations to name the "third party" to which they've attributed a breach. The initial…
Read More »