-
EXPLOITS

SOCaaS Pricing, Hidden Fees, and Investment Value
Dealing with cyber risks is a continuous search for balance: the question is how to stay 24/7 protected without spending…
Read More » -
INSIDER

Cybersecurity Compliance in South Africa
A Continued Cycle South Africa has had a slow approach to compliance with the government regulations and laws set in…
Read More » -
PHISHING
Crypto24 Ransomware Detection: Hackers Hit Large Organizations via Legitimate Tools and Custom Malware to Stay Under the Radar
Ransomware continues to rank among the most critical cyber threats. According to the 2025 Verizon Data Breach Investigations Report (DBIR),…
Read More » -
SPYWARE
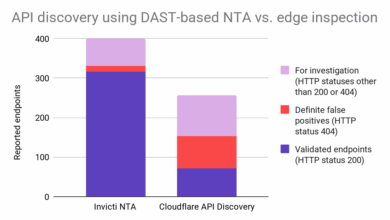
Comparing API Discovery Runtime and Edge Views
Specifically, we took the network-layer API discovery feature powered by Invicti’s DAST-integrated network traffic analyzer (NTA) and compared it to…
Read More » -
WEB ATTACK
Choosing the Right DDoS Protection: 6 Tips for CISOs
On March 10, 2025, X experienced multiple outages due to a large-scale DDoS attack. The attack succeeded because the DDoS…
Read More » -
CLOUD

‘What happens online stays online’ and other cyberbullying myths, debunked
Separating truth from fiction is the first step towards making better parenting decisions. Let’s puncture some of the most common…
Read More » -
EXPLOITS

Broken Chains of Trust. To me, it is all make believe | by Vicente Aceituno Canal | The CISO Den | Aug, 2025
To me, it is all make believe Press enter or click to view image in full size Have you ever…
Read More » -
INSIDER
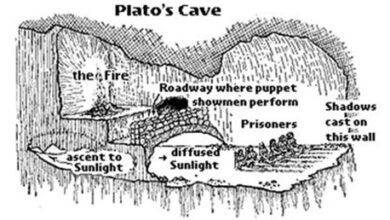
Cybersecurity Shadows: Plato’s Cave and the Dark
“How could they see anything but the shadows if they were never allowed to move their heads?” — Plato, The…
Read More » -
JACKING

What’s Different About the Black Hat Conference, and What’s New in 2025?
I just returned from Black Hat in Las Vegas, and once again, AI dominated all conversations on both the attack…
Read More » -
PHISHING
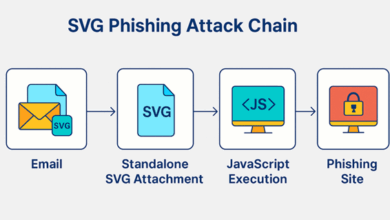
SVG Files: The Hidden Vector in Phishing Attacks
Introduction In the ever-evolving cybersecurity landscape, attackers constantly seek new ways to bypass traditional defences. One of the latest and…
Read More »