-
WEB ATTACK

Cybersecurity Is a Social, Policy, and Wicked Problem
Cybersecurity is a social and policy problem, not a scientific or technical problem. Cybersecurity is also a wicked problem. In…
Read More » -
EXPLOITS

How to report cyber security effectively to the Board — Matt Palmer
How can Chief Information Security Officers and cyber security leaders avoid these board reporting pitfalls? Firstly, you almost certainly have…
Read More » -
CLOUD

Navigating IT Certification Updates Effectively
Staying updated with certification changes is crucial for IT professionals looking to advance their careers. In this article, we will…
Read More » -
INSIDER
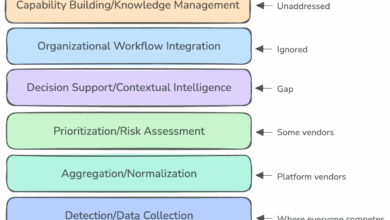
why theory doesn’t match practice
This week, Venture in Security is excited to feature a guest article from Nielet D’Mello. Nielet is a security engineer…
Read More » -
JACKING

Endpoint Protection Gartner Magic Quadrant July 2025
In today’s relentlessly dynamic digital world, organizations face a barrage of new challenges every day—from ever-expanding systems and a surge…
Read More » -
JACKING

Why hackers are targeting agency help desks and key employees to bypass cyber defenses
Government agencies have spent billions building digital fortresses. A new generation of threat actors, however, is circumventing those investments by…
Read More » -
PHISHING

The Ultimate Guide to Using a VPN on Your iPhone
Here is the ultimate guide to using a VPN on your iPhone. Think about this: what is the one thing…
Read More » -
WEB ATTACK
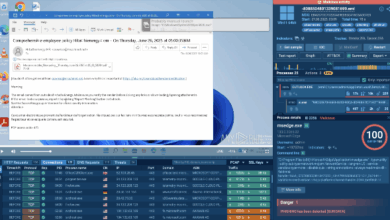
CISO Blueprint: 5 Steps to Enterprise Cyber Threat Resilience
HomeCybersecurity Lifehacks CISO Blueprint: 5 Steps to Enterprise Cyber Threat Resilience Why are SOC teams still struggling to keep up…
Read More » -
SPYWARE

Firewall Security Management Best Practices for Enterprises
Modern organizations depend on databases for everything from customer information to financial transactions. But one of the most pressing challenges…
Read More » -
WEB ATTACK

The Critical Skills Gap That’s Stalling Your Security Career
Date: 11 August 2025 You’ve mastered vulnerability scanning, incident response, and network security. You can configure firewalls in your sleep…
Read More »