-
CLOUD

Weekly Update 462
This will be the title of the blog post: "Court Injunctions are the Thoughts and Prayers of Data Breach Response".…
Read More » -
EXPLOITS

10 steps to effective board leadership on cyber security — Matt Palmer
In just a few years, cyber has transformed from the nerd in the corner into the Kim Kardashian of risk.…
Read More » -
WEB ATTACK

How to Safeguard Your Kids Against Online Predators
How to Safeguard Your Kids Against Online Predators: A Common Sense Guide for Parents – Skip Myers
Read More » -
EXPLOITS
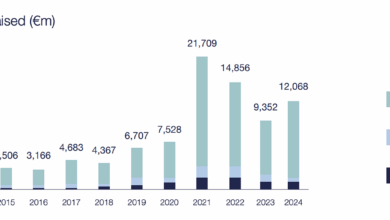
Fewer Cheques, Tougher Checks: Cyber VC in 2025
Hello Cyber Builders 🖖 Cybersecurity is at the top of everyone’s mind, and AI brings more opportunities and threats at…
Read More » -
SPYWARE
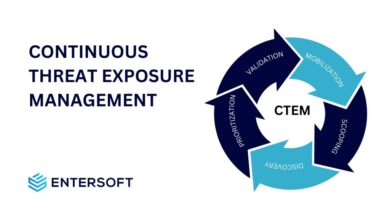
Harnessing Continuous Threat Exposure Management (CTEM) for Business Security
In the dynamic world of cybersecurity, Continuous Threat Exposure Management (CTEM) has emerged as a crucial approach for organizations seeking…
Read More » -
WEB ATTACK
FedRAMP Pen Test Scope vs. Rules of Engagement Explained
FedRAMP has strict requirements for the security of the companies looking to earn their certification. Among the many requirements you…
Read More » -
CLOUD

Maximizing Rewards and Token Benefits
Integrating WeatherXM Stations with FrysCrypto: A Dual Mining Guide Note: This article does not consist of any endorsement of either…
Read More » -
PHISHING
Tarah Wheeler Narrowly Avoids Getting Got
No one is immune from being scammed. Just ask Tarah Wheeler, founder and CEO of Red Queen Dynamics, a company…
Read More » -
WEB ATTACK
Key Network Questions
I wrote this on 7 December 2018 but never published it until today. The following are the “key network…
Read More » -
CLOUD

The Biggest GDPR Fines of 2024 and Previous Years
Although companies have been adapting to the GDPR for years now, the enforcement of GDPR violations is still relatively new…
Read More »