-
EXPLOITS
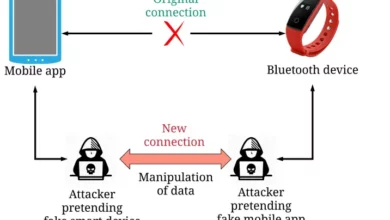
Bluetooth Vulnerability: Mitigating Risks Across Devices
I.Introduction Bluetooth has become an integral technology for billions of smartphones, computers, wearables, and other devices to connect and exchange…
Read More » -
JACKING

Back to Business: Lumma Stealer Returns with Stealthier Methods
Conclusion The Lumma Stealer case exemplifies the adaptability and persistence of modern cybercriminal groups. Despite a major enforcement action, the…
Read More » -
PHISHING
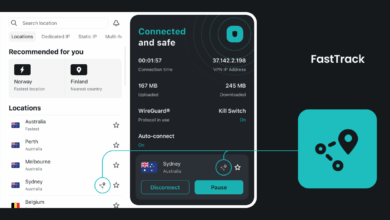
Boost Internet Speed with Next-Level VPN Route Optimization🚀 –
Discover Surfshark FastTrack, the advanced VPN route optimization feature that improves speed, reduces latency, and ensures smooth streaming, gaming, and…
Read More » -
EXPLOITS

Culture Has a Topology. Are You Mapping It?
You can’t change what you can’t see. And you definitely can’t optimize what you can’t map. If culture is the…
Read More » -
INSIDER

Internet ve Telefon Dolandırıcılığı Sosyal Mühendislik -2, Baski
Internet ve Telefon Dolandırıcılığı Sosyal Mühendislik Temelinde teknolojinin yanı sıra insani zaaflarımızın yer aldığı siber dolandırıcılık, literatürdeki adıyla sosyal mühendislik…
Read More » -
JACKING

Do Not Scan These Package QR Codes, FBI Warns
You have been warned — do not scan here. NurPhoto via Getty Images An “impossible” to detect smartphone threat is…
Read More » -
PHISHING

Webinar on demand: The ROI of SOC
Join cybersecurity leaders from G’Secure Labs and Logpoint as they break down what truly defines SOC success. Discover how…
Read More » -
EXPLOITS

What does a good password policy really look like? — Matt Palmer
Passwords should be the easiest area of security. Every organisation has a password policy. Every organisation used passwords. Everyone at…
Read More » -
INSIDER
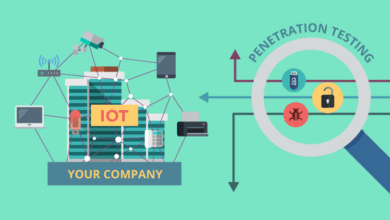
IoT Penetration Testing Strategy
Gartner expects more than 65% of enterprises (for reference, it was only 30% in 2017) to adopt IoT solutions by…
Read More » -
SPYWARE

What Is Managed Detection and Response and Its Key Benefits
Cybersecurity threats today are more advanced, persistent, and targeted than ever before. Traditional defenses such as firewalls and antivirus software…
Read More »