-
CLOUD
A Comprehensive Guide for Efficient Cryptocurrency Mining
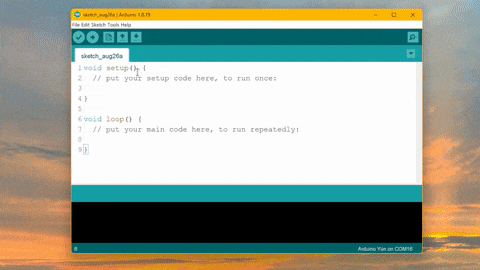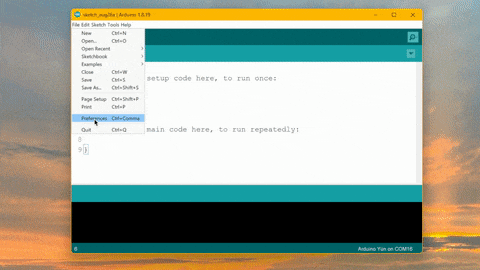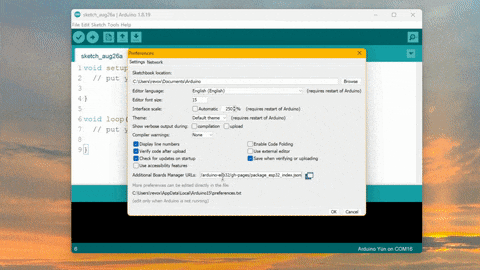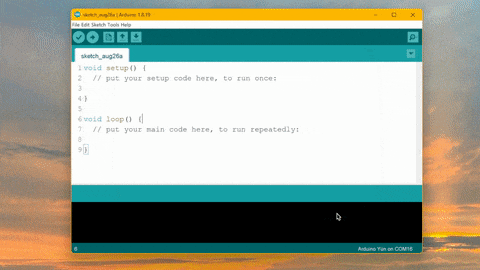
How to Mine Duinocoin on ESP32 Have you ever wondered how to mine Duinocoin on your ESP32 device efficiently? In…
Read More » -
EXPLOITS
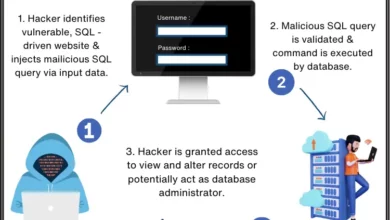
Defend Your Apps: SQL Injection Prevention Guide
Introduction In the era of digitalization, data security has become a paramount concern. Every day, countless businesses and organizations rely…
Read More » -
PHISHING

Carina Follows Her Heart Into a Crypto Scam
No one’s too smart for a well-designed scam. Case in point, neuroscientist, triathlete Carina who thought the finance bro she…
Read More » -
SPYWARE

Temporary Workaround for CrowdStrike-Induced Windows Outages
As you might be aware, there has been a major outage affecting Windows systems globally due to a recent update…
Read More » -
WEB ATTACK

Gaming Security for Kids
Gaming Security for Kids: Navigating the Disciplines of Fun and Safety
Read More » -
CLOUD
Use Built-In Phishing Reporting in Outlook or Gmail
The Current Reality: Chaos in Reporting Does the following sound familiar? Teams message: “Hey, I just got an email that…
Read More » -
INSIDER

What Is Social Engineering in Cybersecurity?
How many times have you heard the phrase “don’t trust strangers”? The key point today is that many strangers disguise…
Read More » -
PHISHING

Compounding Calculator: The Secret Tool Millennials Should Use
In this post, I will talk about the compounding calculator, which is the secret tool millennials should use. Today’s world…
Read More » -
SPYWARE
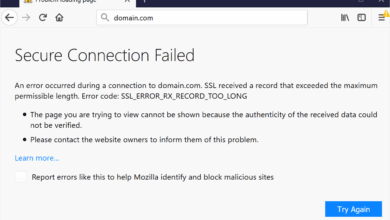
Fix SSL_ERROR_RX_RECORD_TOO_LONG in Firefox – Quick Guide
When Firefox throws up the error SSL_ERROR_RX_RECORD_TOO_LONG, it’s not just a random glitch. It’s Firefox’s way of protecting you when…
Read More » -
WEB ATTACK
List of Tasks for Providers
Most of the time on the Ignyte blog, we talk about overarching security frameworks like FedRAMP, CMMC, and ISO 27001.…
Read More »