CLOUD
-
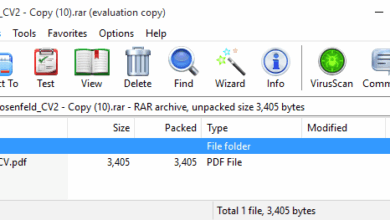
RomCom and others exploiting zero-day vulnerability
ESET researchers have discovered a previously unknown vulnerability in WinRAR, being exploited in the wild by Russia-aligned group RomCom. This…
Read More » -
A Comprehensive Guide for Efficient Cryptocurrency Mining
How to Mine Duinocoin on ESP32 Have you ever wondered how to mine Duinocoin on your ESP32 device efficiently? In…
Read More » -
Use Built-In Phishing Reporting in Outlook or Gmail
The Current Reality: Chaos in Reporting Does the following sound familiar? Teams message: “Hey, I just got an email that…
Read More » -
Welcoming Guardio to Have I Been Pwned’s Partner Program
I’m often asked if cyber criminals are getting better at impersonating legitimate organisations in order to sneak their phishing attacks…
Read More » -

WinRAR zero-day exploited in espionage attacks against high-value targets
The attacks used spearphishing campaigns to target financial, manufacturing, defense, and logistics companies in Europe and Canada, ESET research finds…
Read More » -

What the data from +200.000 phishing emails learns us
Do you learn anything from sending thousands of phishing emails? YES, you do, and we want to share it with…
Read More » -

Using AWS ACM with xrdp on Ubuntu ~ Since We Can Export Certs Now | by Teri Radichel | Cloud Security | Jul, 2025
Well, AI helped a little but I had to do a lot myself and it took WAY. TOO. LONG. ~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~…
Read More » -

Weekly Update 464
I think the most amusing comment I had during this live stream was one to the effect of expecting me…
Read More » -

How the always-on generation can level up their cybersecurity game
Digital natives are comfortable with technology, but may be more exposed to online scams and other threats than they think…
Read More » -

Maximize Connectivity with USB Standards & Ports Guide
USB standards and ports play a crucial role in connecting various devices to a computer or other electronic devices. Understanding…
Read More »