CLOUD
-
Use Microsoft Defender to strengthen your email security
Do your company use Office365? A lot of you do. Did you know, that Microsoft Defender is one of the…
Read More » -
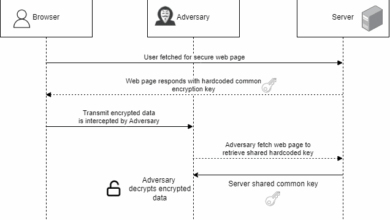
How Poor Cryptographic Practices Endanger Banking Security
In today’s digital age, financial institutions rely heavily on encryption to protect sensitive data in their banking applications. However, despite…
Read More » -

Understanding Signaling System 7 (SS7)
The Signaling System 7 (SS7) is a set of protocol suite telecommunication networks used to share information across the global…
Read More » -

Focus. Re-evaluating what you are doing in the… | by Teri Radichel | Cloud Security | Aug, 2025
Re-evaluating what you are doing in the face of AI — is it worth it? 27 min read · Aug…
Read More » -

Weekly Update 465
How much tech stuff do I have sitting there in progress, literally just within arm's reach? I kick off this…
Read More » -

Why organizations are turning to rapid, trustworthy MDR
How top-tier managed detection and response (MDR) can help organizations stay ahead of increasingly agile and determined adversaries 19 Aug…
Read More » -

Mastering Range and Speed with External Antennas
Modifying the Helium Mobile Indoor WiFi Hotspot with External Antennas for Increased Range and Speed In a world increasingly reliant…
Read More » -
Summer Releases – Auto Phishing, Benchmarking and More
The first six months of 2025, we’ve released a bunch of cool stuff. Auto phishing, benchmark data, and much more.…
Read More » -

A Message from Our CEO
Hello everyone, I’m excited to share some big news with you today. WeSecureApp is evolving into Strobes Security. This isn’t…
Read More » -

Top 5 Open Source Firewall for Network Security
A firewall is a security system that is used to control network traffic and prevent unauthorized access to a network.…
Read More »