EXPLOITS
-

How to get fast board buy-in for your cyber security project — Matt Palmer
To experts, the business case for cyber security change programmes can seem clear as day — it can be hard…
Read More » -

How AI Will Redefine the 12 Cybersecurity Platforms
Hello Cyber Builders 🖖 We’re back at it—diving deeper into the world of cybersecurity platforms that are shaping the future.…
Read More » -

Does moving to the cloud mean compromising on security? — Matt Palmer
The transition to cloud computing is an evolution that many organisations are still undertaking to improve efficiency, scalability, and flexibility…
Read More » -

How to report cyber security effectively to the Board — Matt Palmer
How can Chief Information Security Officers and cyber security leaders avoid these board reporting pitfalls? Firstly, you almost certainly have…
Read More » -

10 steps to effective board leadership on cyber security — Matt Palmer
In just a few years, cyber has transformed from the nerd in the corner into the Kim Kardashian of risk.…
Read More » -
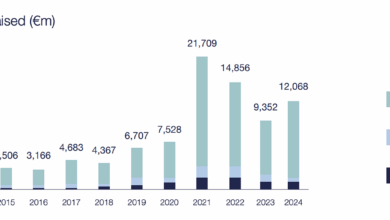
Fewer Cheques, Tougher Checks: Cyber VC in 2025
Hello Cyber Builders 🖖 Cybersecurity is at the top of everyone’s mind, and AI brings more opportunities and threats at…
Read More » -
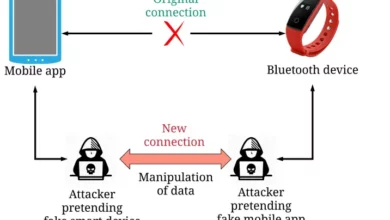
Bluetooth Vulnerability: Mitigating Risks Across Devices
I.Introduction Bluetooth has become an integral technology for billions of smartphones, computers, wearables, and other devices to connect and exchange…
Read More » -

Culture Has a Topology. Are You Mapping It?
You can’t change what you can’t see. And you definitely can’t optimize what you can’t map. If culture is the…
Read More » -

What does a good password policy really look like? — Matt Palmer
Passwords should be the easiest area of security. Every organisation has a password policy. Every organisation used passwords. Everyone at…
Read More » -

A Journey to the Highest Cybersecurity Maturity: Part 6
Requests Cycle Continue reading on The CISO Den »
Read More »