EXPLOITS
-
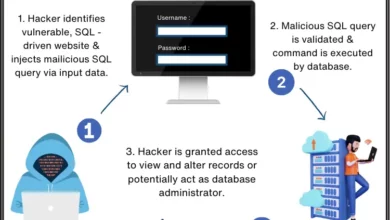
Defend Your Apps: SQL Injection Prevention Guide
Introduction In the era of digitalization, data security has become a paramount concern. Every day, countless businesses and organizations rely…
Read More » -

Why is Jersey introducing a new Cyber Security Law?
In 2021 I took a new role as Director of Jersey’s newly formed cyber response unit. We’ve come a long…
Read More » -
My Story from the Spanish Blackout
Hello Cyber-Builders 🖖 In 2017, I published a paper with NATO experts on what had happened to the Ukrainian power…
Read More » -

Quantum-ready data security: Safeguarding information beyond binary
Abstract In the rapidly advancing landscape of quantum computing, the potential for revolutionary processing power also brings forth significant challenges…
Read More » -

Trust, Rebuilt with Analog Signals
As AI-generated content grows more sophisticated and malicious actors harness synthetic media at scale, the digital domain is becoming increasingly…
Read More » -

Applying agile principles to public sector change — Matt Palmer
Right now at Jersey Cyber Security Centre we have two critical change projects: 1) creating and delivering a new public…
Read More » -

Why Nation-States Are Hacking the Power That Runs the World
“If you want to weaken a nation without firing a shot, start by flipping the switch.” Hello Cyber Builders 🖖,…
Read More » -

A Journey to the Highest Cybersecurity Maturity: Compliance, Part 8 | by Vicente Aceituno Canal
Compliance Management Press enter or click to view image in full size Photo by Anne Nygård on Unsplash Previously in…
Read More » -

Unveiling the Secrets of the Dark Web
Introduction The internet, often regarded as a vast and mysterious realm. It is not a singular entity but rather a…
Read More » -
The Role of Automation – Data Privacy Manager
The Saudi Arabian Personal Data Protection Law (PDPL) marks a significant milestone in the kingdom’s efforts to protect individuals’ personal…
Read More »