EXPLOITS
-

Training for Offense, Not Just Defense
Some topics in cybersecurity stir discomfort. Here’s one: what if your people weren’t just trained to detect risk, but to…
Read More » -

The Real Meaning Behind the Jargon — Matt Palmer
Cyber security is often conflated with the term confidentiality, but that is not correct. Traditionally, professionals tend to define it…
Read More » -

When the Grid Gets Smart, the Threat Gets Smarter
Hello Cyber Builders 🖖 This is the third and final post in my series on cybersecurity and power grids. Today,…
Read More » -

A Journey to the Highest Cybersecurity Maturity: Performance, Part 9
Activity Management Continue reading on The CISO Den »
Read More » -
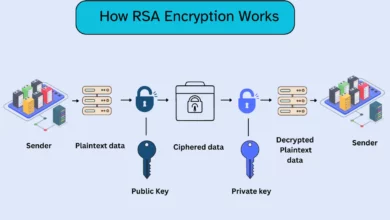
Enduring Power of RSA Encryption in Securing Network Communications
Introduction As organizations and individuals rely increasingly on digital systems to communicate and share sensitive information online, robust encryption methods…
Read More » -

What is a Data Subject Access Request (DSAR) – Data Privacy Manager
When the General Data Protection Regulation (GDPR) was enforced back in 2018, it was set out to give individuals control…
Read More » -

Why We Must Embrace Risk and Learn From Incidents — Matt Palmer
Welcome to Incidentally: Why We Must Embrace Risk and Learn From Incidents As humans, we don’t take risks just for…
Read More » -

What Is Your Digital Footprint Revealing to Attackers—and How Can You Turn It into a Defense?
Your online presence—social media posts, web registrations, breach data—creates a digital footprint that attackers can study and exploit without you…
Read More » -

The Only AI Tool AppSec Needs. Obviously
Software quietly runs the systems we rely on—our banks, logistics, communication, and cars. But for many AppSec teams, that software…
Read More » -

A Journey to the Highest Cybersecurity Maturity: Quality, Part 10
Quality Management Continue reading on The CISO Den »
Read More »