EXPLOITS
-

Is hacktivism acceptable? — Matt Palmer
This week I attended CSO Online’s CSO Security Summit in London, which was tracked into protection and culture tracks. One…
Read More » -

Deep Packet Inspection vs TCP Analysis: What NDR Brings to the Table
Network security engineers don’t mess around when sophisticated threats target enterprise infrastructure. Yet many security teams struggle with a fundamental…
Read More » -

CyGO Entrepreneurs playbook, Glev Illustrated
Hello, Cyber Builders 🖖 I’m closing out our July series on application security with a story that doesn’t follow the…
Read More » -

CISO, how do you measure maturity? | by Vicente Aceituno Canal | The CISO Den
No, is not how you thought Press enter or click to view image in full size ISMS maturity is not…
Read More » -
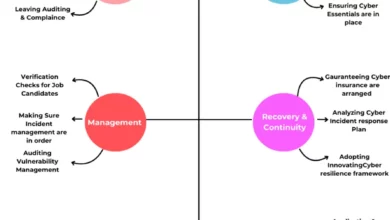
A CISO’s Take on Cyber Protection
Introduction In a rapidly evolving business landscape, cybersecurity is paramount amidst frequent cyber-attacks, emphasizing the crucial role of a Chief…
Read More » -

PDPA Compliance Checklist for Singapore Businesses – Data Privacy Manager
A Practical Blueprint for PDPA Compliance The Personal Data Protection Act (PDPA) is not just a legal formality — it’s…
Read More » -

The Behavioral Foundations of Effective Human Risk Management
Human Risk Management (HRM) is often described as a framework or a set of processes, but at its heart, HRM,…
Read More » -

Introducing Guernsey Cyber Security Centre — Matt Palmer
Since 2021, I’ve been building Jersey Cyber Security Centre (JCSC). As a cyber defence capability for an island state and…
Read More » -

Indicators of Compromise in Threat Intelligence: Real-Time Action
Organizations face mounting pressure from cyber threats that exploit detection delays. Industry data shows breach costs averaging $4.45 million per…
Read More » -
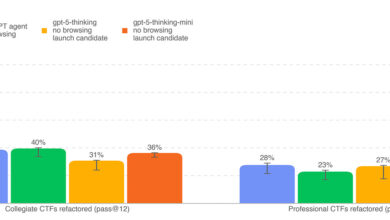
GPT-5 Is Around the Corner. Stop Treating AI Like a Threat—Hire It.
Hello Cyber Builders 🖖, Every time a new AI model drops, the same debate starts: Is it safe? Could it…
Read More »