INSIDER
-
Scaling Sophos to $1B+ revenue and defending the 350M overlooked businesses
In this episode of Inside the Network, we sit down with Joe Levy, CEO of Sophos, a 40-year-old cybersecurity company…
Read More » -
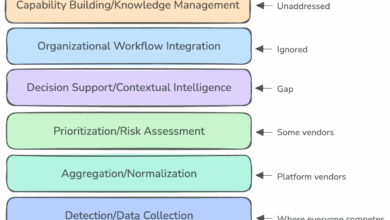
why theory doesn’t match practice
This week, Venture in Security is excited to feature a guest article from Nielet D’Mello. Nielet is a security engineer…
Read More » -

Internet ve Telefon Dolandırıcılığı Sosyal Mühendislik -2, Baski
Internet ve Telefon Dolandırıcılığı Sosyal Mühendislik Temelinde teknolojinin yanı sıra insani zaaflarımızın yer aldığı siber dolandırıcılık, literatürdeki adıyla sosyal mühendislik…
Read More » -
IoT Penetration Testing Strategy
Gartner expects more than 65% of enterprises (for reference, it was only 30% in 2017) to adopt IoT solutions by…
Read More » -

What Is Social Engineering in Cybersecurity?
How many times have you heard the phrase “don’t trust strangers”? The key point today is that many strangers disguise…
Read More » -
Think Before You Click: EPI PDF’s Hidden Extras
Authored by: Anuradha & Prabudh PDF converting software can be super helpful. Whether you’re turning a Word document into a…
Read More » -
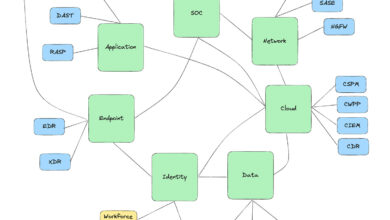
You don’t start a platform, you earn the right to become one
In cybersecurity, “platform” is the most abused word, used by every startup with two engineers and a feature flag. We…
Read More » -

CIO Imperatives: Dr. Timothy C. Summers on Digital Trust, AI, and Why a Trusted CISO is Non-Negotiable 1
CIO Imperatives: Dr. Timothy C. Summers on Digital Trust, AI, and Why a Trusted CISO is Non-Negotiable In an era…
Read More » -

Black, White and Gray Box
Editor’s note: On the example of network security, Uladzislau describes the essence, pros and cons of black, gray, and white box…
Read More » -
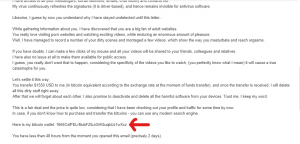
Don’t Be a Victim! Blackmail Scam Emails Exposed
Sextortion scam emails have become a disturbingly common occurrence in people’s inboxes. These menacing messages claim the sender has hacked…
Read More »