JACKING
-

Proactive Security for CVE-2025-53770 and CVE-2025-53771 SharePoint Attacks
Post-Exploitation Analysis Our analysis reveals that threat actors are leveraging the initial compromise for comprehensive enterprise reconnaissance and data theft.…
Read More » -

Meet This Year’s Europe Community Meeting Keynote Speaker, Bernie Collins
This episode of Coffee with the Council is brought to you by our podcast sponsor, Feroot. Welcome to our…
Read More » -

Heimdal® Achieves Fifth Consecutive ISAE 3000 SOC 2 Type II Certification
COPENHAGEN, Denmark, July 23, 2025 – Heimdal is proud to announce that it has once again secured the ISAE 3000…
Read More » -
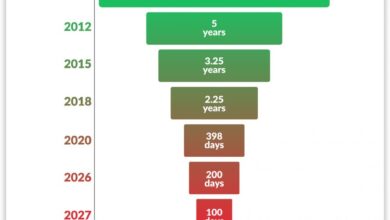
Industry Leaders Approve the Move to a 47-Day SSL Certificate Validity Period
By 2029, SSL/TLS certificates will be valid for a maximum of 1.5 months. Here’s what to know about the certificate…
Read More » -

Here’s how to spot and stop them
The conversational AI market is exploding. Grand View Research suggests it’s set to jump from $11.58 billion in 2024 to…
Read More » -
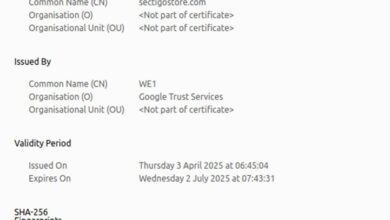
10 Digital Identity Examples for Small Business Owners
VikingCloud reports that one in five SMBs believe they’d be forced out of business if they fell prey to a…
Read More » -

Amazon Security Lake & Trend Vision One™ for Proactive Security
Introduction It’s no secret that security is one of the main challenges of application development and modernization. It plays a…
Read More » -

The Impact of Security Breaches on Educational Institutions
This blog was originally published by Bravura here. Educational institutions oversee hundreds or thousands of students and faculty members…
Read More » -
Attack Surface Management Software: Top 10 Vendors
Key Takeaways: What is attack surface management? Why is attack surface management important? What are the best ASM vendors? Over…
Read More » -
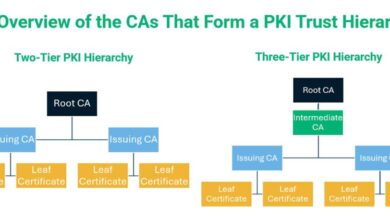
Demystifying PKI Technology: An Essential Guide for IT Security Professionals
Learn everything you need to know about PKI technology in IT security that enables organizations to establish trust in a…
Read More »