JACKING
-

Non-Human Identities: The unseen workforce driving AI-era security
This blog was originally published by iDMig here. Non-human identities (NHIs) are front and center Throughout the conferences I’ve attended,…
Read More » -

5 Steps to Secure Gmail Emails and Attachments
Gmail is the world’s most popular email platform, boasting over 1.8 billion users worldwide and holding a significant share of…
Read More » -

Fortinet VPNs Under Coordinated Attack
Time for your Weekly Cyber Snapshot with Adam Pilton, former Cybercrime Investigator, currently Cybersecurity Advisor.The five major cyber stories this…
Read More » -
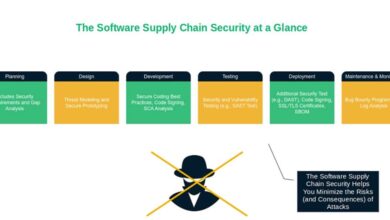
The Ultimate Guide to Software Supply Chain Security Risks, Threats, and Mitigations
In July 2025, a core node package manager (npm) package with 28+ million downloads per week was compromised, exposing millions…
Read More » -

What’s Different About the Black Hat Conference, and What’s New in 2025?
I just returned from Black Hat in Las Vegas, and once again, AI dominated all conversations on both the attack…
Read More » -

CEO Eva Chen: Leadership, Innovation & AI’s Future
As a woman working at Trend Micro, I’m proud to be part of a company led by Eva Chen, our…
Read More »