PHISHING
-
NIST 800-53 Compliance Checklist and Security Controls Guide
Ensuring compliance with NIST SP 800-53 is critical for aligning your cybersecurity efforts with federal standards. This popular cybersecurity framework…
Read More » -

How Dealerships Can Protect Their Customers’ Financial Data
Dealerships handle sensitive information, such as credit applications and personal financial records, daily. A data breach can lead to profound…
Read More » -

What You Need to Know
You encounter the love of your life online, never meeting them in person. Or you get an email about an…
Read More » -
The Ultimate Guide to SERP Scraper APIs: Power, Performance & Providers
Here is the ultimate guide to SERP Scraper APIs. Read on. Search engine results pages (SERPs) are the mines for…
Read More » -

Healthcare Organizations at Risk: Managing Human Vulnerability in Cybersecurity
The battle against cybercrime continues to be a significant topic for organizations across all industries, however the threat to the…
Read More » -
What is Attack Surface Management? Tools and Best Practices
Attack surface management (ASM) is a fundamental cybersecurity approach that involves continuously identifying, analyzing, remediating, and monitoring all the current…
Read More » -

The Ultimate Guide to Using a VPN on Your iPhone
Here is the ultimate guide to using a VPN on your iPhone. Think about this: what is the one thing…
Read More » -
Tarah Wheeler Narrowly Avoids Getting Got
No one is immune from being scammed. Just ask Tarah Wheeler, founder and CEO of Red Queen Dynamics, a company…
Read More » -
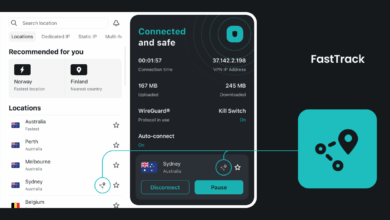
Boost Internet Speed with Next-Level VPN Route Optimization🚀 –
Discover Surfshark FastTrack, the advanced VPN route optimization feature that improves speed, reduces latency, and ensures smooth streaming, gaming, and…
Read More » -

Webinar on demand: The ROI of SOC
Join cybersecurity leaders from G’Secure Labs and Logpoint as they break down what truly defines SOC success. Discover how…
Read More »