SPYWARE
-

Server side template injection — SSTI vulnerability ⚠️ | by Ivan Novikov
Introduction There is hardly any software development or other linked elements that haven’t fallen into the trap of cyber vulnerabilities.…
Read More » -

The Role of EDR in Real-Time Threat Detection & Response
Understanding how EDRs work requires examining the sophisticated mechanisms that enable these systems to detect, analyze, and respond to cybersecurity…
Read More » -
Google’s Strongest Security for Mobile Devices
Posted by Il-Sung Lee, Group Product Manager, Android Security Protecting users who need heightened security has been a long-standing commitment…
Read More » -

5 Key Challenges When Adopting AI and Machine Learning in Cybersecurity
5 Key Challenges When Adopting AI and Machine Learning in Cybersecurity AI and machine learning (ML) are rapidly becoming cornerstones…
Read More » -

Black-Box vs White-Box Penetration Testing Explained
Introduction When securing your applications, choosing the right penetration testing methodology is crucial. Two widely used techniques are Black-Box Testing…
Read More » -
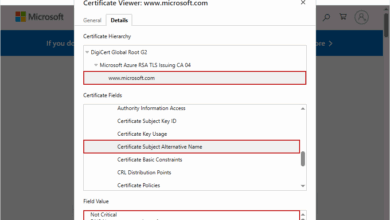
What is a SAN SSL Certificate?
If an organization handles multiple number of domains, subdomains, or internal services, it is likely to become inefficient or error-prone.…
Read More » -

What is Cross Site Request Forgery CSRF | Example and Methods of protection | by Ivan Novikov
Organizations aspiring for all-around resource security against the damage-causing cyber vulnerabilities must upgrade their knowledge and get acquainted with all…
Read More » -

Without Fraud, There Would be No Tesla
The American market regulation system is so broken, it has taken ten years and hundreds of unnecessary deaths for mainstream…
Read More » -

Best Solutions for Cyber Defense
The cybersecurity market continues to grow as organizations face increasingly sophisticated threats that require advanced monitoring and response capabilities. Security…
Read More » -
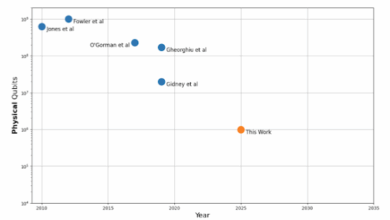
Tracking the Cost of Quantum Factoring
Google Quantum AI’s mission is to build best in class quantum computing for otherwise unsolvable problems. For decades the quantum…
Read More »