SPYWARE
-

What Makes Deep Learning in Cybersecurity Different and Why it Matters for Cybersecurity
What Makes Deep Learning in Cybersecurity Different and Why it Matters for Cybersecurity AI and machine learning are rapidly reshaping…
Read More » -

#What is Cloud Security Testing for Multi-Cloud
Introduction As businesses increasingly adopt multi-cloud environments for greater flexibility, they also face unique security challenges. Each cloud provider has…
Read More » -
How Invicti built the security engine of the future for its Application Security Platform
One engine to rule them all Our recent launch marked a significant achievement for Invicti, with the successful integration of…
Read More » -

What is an SSL certificate ❓ Meaning and Types | by Ivan Novikov
Introduction Website/application owners have tons of aspects to look into. However, ensuring end-to-end security ranks top as it is the…
Read More » -

How Ethics Breaks Linear Thinkers
Think about the very concept of “waxing” and “waning” of a moon in orbital cycle. Such predictable rotation is mischaracterized…
Read More » -

“SOC Benefits for Small Businesses: Why You Need Them
Small businesses face an uncomfortable reality in today’s digital world. Cyber criminals view them as attractive targets precisely because many…
Read More » -
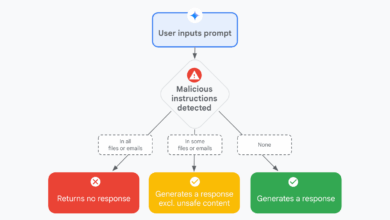
Mitigating prompt injection attacks with a layered defense strategy
With the rapid adoption of generative AI, a new wave of threats is emerging across the industry with the aim…
Read More » -

IDS vs IPS: What’s the Difference and Why Do You Need Both?
IDS vs IPS: What’s the Difference and Why Do You Need Both? The impact of data breaches is growing all…
Read More » -

How Entersoft Empowers SEBI Entities in Cybersecurity & Resilience |
Introduction In an increasingly digital and interconnected world, cybersecurity for financial institutions is paramount. Recognizing this, the Securities and Exchange…
Read More » -
What’s the Difference and Which One Do You Need?
Phishing is outpacing defenses, and inboxes are flooded with lookalike senders. Hence, visual trust has become a frontline necessity and…
Read More »