SPYWARE
-

What is threat modeling ❓ Definition, Methods, Example | by Ivan Novikov
Threat modeling is a method for upgrading the security of an application, system, or business process by distinguishing objections and…
Read More » -
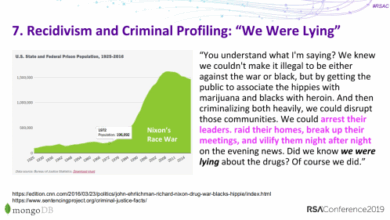
Study Shows How High Crime Rates Can Be Proof of Better Policing
A recent study by Simmrin Law Group claiming to identify “states where Americans face the highest risk of false crime…
Read More » -

How a Managed SOC Enhances Incident Response
Cybersecurity incidents have become a when, not if, reality for organizations across all industries. The speed and effectiveness of incident…
Read More » -
Advancing Protection in Chrome on Android
Posted by David Adrian, Javier Castro & Peter Kotwicz, Chrome Security Team Android recently announced Advanced Protection, which extends Google’s…
Read More » -

IPS Tools in Cybersecurity: Still Essential in 2025?
IPS Tools in Cybersecurity: Still Essential in 2025? Cybersecurity threats are no longer limited to basic malware or isolated breaches.…
Read More » -

Why Application Detection and Response (ADR) is Essential for Security
Introduction: In an age where digital transformation is at the core of every business, securing applications has become crucial. While…
Read More » -

PolarEdge, Gayfemboy, and EAGLEDOOR: Botnets and APTs Exploit GeoServer Vulnerability
Cybercriminals and advanced persistent threat (APT) actors are increasingly converging on a stealth-first, profit-driven, and persistence-focused model of operations. Recent…
Read More » -
What is BIMI | Brand Indicators for Message Identification
Why do even legitimate marketing emails get ignored? It’s not always the message it’s how the email looks. Years of…
Read More » -

Why AI Bubble Talk is Pop Nonsense
For all the times I’ve said the AI hype is way too overheated, I also dislike extreme cold. Where did…
Read More » -

Top Security Operations Center Practices for SMEs
A Security Operations Center represents a centralized approach to monitoring, detecting, and responding to cybersecurity threats. For SMEs, the challenge…
Read More »