SPYWARE
-
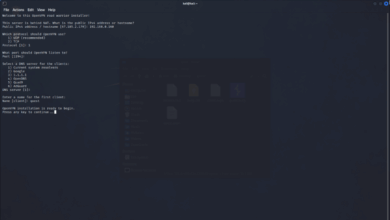
Setting Up a Pentesting Environment for the Meta Quest 2
With the advent of commercially available virtual reality headsets, such as the Meta Quest, the integration of virtual and augmented…
Read More » -
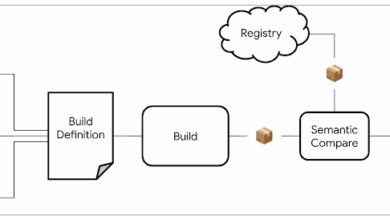
Open Source, Rebuilt to Last
Today we’re excited to announce OSS Rebuild, a new project to strengthen trust in open source package ecosystems by reproducing…
Read More » -
The Role of Wireless Intrusion Detection: Guard Against Invisible Threats
Guarding Against Invisible Threats: The Role of Wireless Intrusion Detection Wireless connectivity is foundational to modern business. From corporate offices…
Read More » -

SAST vs. DAST: Choosing the Right Approach for Application Security
Introduction With the increasing complexity of web applications and the rise in sophisticated cyber threats, implementing a robust security testing…
Read More » -
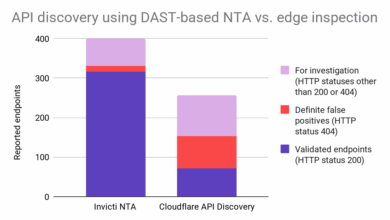
Comparing API Discovery Runtime and Edge Views
Specifically, we took the network-layer API discovery feature powered by Invicti’s DAST-integrated network traffic analyzer (NTA) and compared it to…
Read More » -

What Is Containers-as-a-Service (CaaS)?
Modern software teams are increasingly adopting container technology to deploy applications more efficiently. However, running hundreds of containers at scale…
Read More » -
How Shorter TLS Lifespans Will Change SSL Renewal Frequency
When SSL/TLS certificates first became standard for securing websites, it was common to install one and not think about it…
Read More » -
Global data breach costs hit all-time high
EXECUTIVE SUMMARY: Global data breach costs have hit an all-time high, according to IBM’s annual Cost of a Data Breach…
Read More »