WEB ATTACK
-
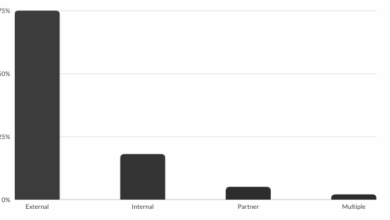
2023 Breaches and Incidents: Personal Notes
Introduction In today’s digital landscape, the prevalence of cyber threats and incidents has become a significant concern for individuals, organizations,…
Read More » -
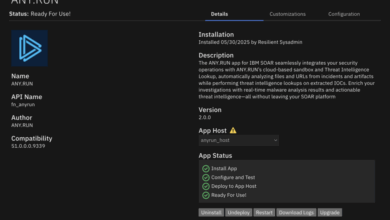
QRadar SOAR App, Free TI Lookup, Detection Rules
HomeService Updates Release Notes: QRadar SOAR App, TI Lookup Free Access, and 2,900+ New Detection Rules July brought powerful new…
Read More » -

Review: Adversarial AI Attacks, Mitigations, and Defense Strategies
Adversarial AI Attacks, Mitigations, and Defense Strategies shows how AI systems can be attacked and how defenders can prepare. It’s…
Read More » -
Digital Privacy Risks During Family Breakdowns
Date: 13 August 2025 After a family breaks up or a relationship ends, digital privacy becomes more important but is…
Read More » -

-
Who Owns CMMC Evidence Collection in a Small Business?
The Cybersecurity Maturity Model Certification, CMMC, is a critical part of ensuring robust and equal information security from top to…
Read More » -
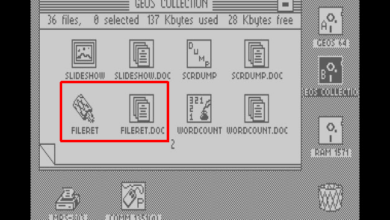
Retrieving Deleted Files on the Commodore C64 in 1987
When I was a sophomore in high school, from 1987 to 1988, my friend Paul and I had Commodore C64…
Read More » -

CRITICAL INSIGHT Q&A: The high-stakes push to safeguard ‘FirstNet’ broadband spectrum
First responders have long depended on calling for backup and clearing the airwaves. Since its launch in 2018, FirstNet—America’s public…
Read More » -

Leading the uncertainty: the decision-driven approach
Many of my readers know me as a cybersecurity expert. More than 12 years of blogging on “security stuff”, malware…
Read More » -
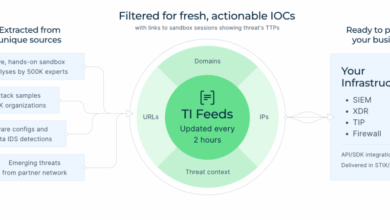
ANY.RUN & Microsoft Sentinel: Catch Emerging Threats with Real-Time Threat Intelligence
HomeIntegrations & connectors ANY.RUN & Microsoft Sentinel: Catch Emerging Threats with Real-Time Threat Intelligence ANY.RUN now delivers Threat Intelligence (TI)…
Read More »