WEB ATTACK
-

What Are Normal Users Supposed to Do with IDS Alerts from Network Gear?
Probably once a week, I see posts like this in the r/Ubiquiti subreddit. Ubiquiti makes network gear that includes an…
Read More » -

SHARED INTEL Q&A: Rethinking Zero Trust to close the widening gap on file-borne threats
For years, “Zero Trust” has reshaped cybersecurity architecture — pushing organizations to move beyond the perimeter and reframe everything around…
Read More » -
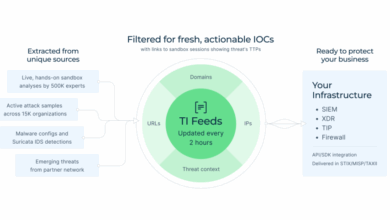
Bridging the Threat Intelligence Gap in Your SOC: A Guide for Security Leaders
HomeCybersecurity Lifehacks Bridging the Threat Intelligence Gap in Your SOC: A Guide for Security Leaders As we highlighted in our…
Read More » -

What Went Wrong and What We Can Learn
One of the most influential Cryptocurrency platforms in the world, Coinbase, is the latest victim of a headline-making cyber attack.…
Read More » -

The Secret World of Catfishing
The Secret World of Catfishing: Unmasking the Deceptive and Malicious Tactics Used by Scammers to Target YOU!
Read More » -
What Can You Expect From Them?
Part of the process of achieving certification with CMMC is undergoing an audit to validate your security posture across all…
Read More » -

Happy 22nd Birthday TaoSecurity Blog
Happy birthday TaoSecurity Blog, born on this day in 2003! The best way to digest the key lessons from this…
Read More » -

EMERGING TRENDS Q&A: Pentesting goes continuous as Plainsea joins wave reshaping security
Penetration testing has long served as a cornerstone of cybersecurity—a red-team exercise, often once or twice a year, designed to…
Read More » -
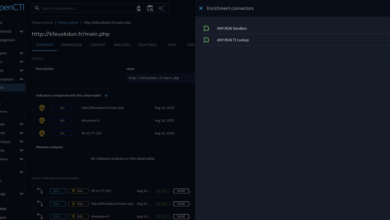
ANY.RUN & OpenCTI: Transform SOC for Maximum Performance
HomeIntegrations & connectors ANY.RUN & OpenCTI: Transform SOC for Maximum Performance Editor’s note: The current article was originally published on…
Read More » -

Why satellite cybersecurity threats matter to everyone
Satellites play a huge role in our daily lives, supporting everything from global communications to navigation, business, and national security.…
Read More »