Firewall Security Management Best Practices for Enterprises

Modern organizations depend on databases for everything from customer information to financial transactions. But one of the most pressing challenges in cybersecurity is ensuring that these repositories remain safe from attackers. The phrase “the security database on the server” reflects not just the technical structure of stored credentials and access controls but also the broader set of risks that come with managing sensitive information. Protecting critical data requires a layered approach that combines strong configurations, monitoring, and policies designed to prevent unauthorized access or tampering.
Understanding the Security Database on the Server
The term security database on the server typically refers to the collection of authentication details, permissions, and user accounts that regulate who can access a system. This data is essential for enforcing identity management and ensuring that only trusted users are allowed into critical environments. If compromised, it provides attackers with the keys to an organization’s most sensitive assets.
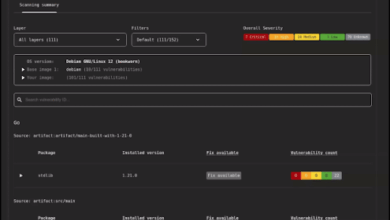
Beyond authentication, security databases often hold logs, access histories, and configuration files. These are valuable to defenders but equally attractive to adversaries. Misconfigured servers, weak passwords, or outdated software can expose this sensitive information to breaches. For this reason, ensuring robust database server security has become one of the top priorities for IT and security teams.
Common Risks Facing Database Servers

Misconfigurations
Servers that are deployed with default settings or overly permissive rules expose unnecessary services. Attackers often exploit these weak points to gain entry.
Weak Authentication
Poor password policies, lack of multifactor authentication, and insecure credential storage make it easier for attackers to compromise accounts and escalate privileges.
Unpatched Vulnerabilities
Outdated database engines or operating systems frequently contain known vulnerabilities. Without timely patching, these flaws provide attackers with direct access.
Insider Threats
Not all risks come from outside. Employees or contractors with excessive privileges may intentionally or unintentionally expose sensitive data.
How to Secure Database Server Environments
Enterprises must apply multiple safeguards to ensure comprehensive protection. The following best practices highlight how to secure database server deployments effectively:
- Harden configurations – disable unused services, enforce encryption for data in transit and at rest, and restrict administrative interfaces.
- Enforce strong authentication – implement multifactor authentication, enforce password complexity, and store credentials securely.
- Apply regular patching – maintain a strict schedule for updating database engines, plugins, and operating systems.
- Monitor continuously – collect and analyze logs to detect anomalies, integrating with SIEM solutions for broader visibility.
- Restrict privileges – apply the principle of least privilege, ensuring users only have access to the data they need.
- Conduct regular assessments – as outlined in Vulnerability Assessment, scheduled testing helps identify hidden weaknesses before attackers do.
Advanced Database Server Security Practices
Beyond basic protections, enterprises should adopt advanced controls to strengthen resilience:
- Network segmentation – isolate database servers from general user networks to reduce exposure.
- Data masking and encryption – use masking techniques for sensitive fields and encrypt backups as well as primary datasets.
- Behavioral analytics – monitor queries for unusual patterns that may indicate misuse or exfiltration attempts.
- Incident response integration – link monitoring systems with Managed Detection & Response for faster detection, investigation, and containment of breaches.
- Policy alignment – build security rules that align with regulatory frameworks, as detailed in How to Create a Cybersecurity Policy.
Database Security in the Cloud Era
The widespread migration to cloud platforms has fundamentally changed how organizations store, access, and protect their most valuable information. While the cloud offers scalability, cost efficiency, and flexibility, it also introduces new complexities that can undermine security if not properly addressed. Misconfigured cloud databases remain one of the leading causes of breaches, often exposing vast amounts of sensitive data to the internet simply because access controls were not set correctly. Overly broad permissions, where users or applications are granted more access than they require, compound the problem by making it easier for attackers or insiders to exploit weaknesses.
Another challenge lies in the shared responsibility model, which defines a split between what the cloud provider secures and what the customer must secure. Many organizations misunderstand this division, assuming that cloud providers manage everything, when in reality, customers are still accountable for areas like configuration, identity management, and data-level encryption. High-profile incidents consistently demonstrate how even minor oversights, such as leaving an unsecured database endpoint exposed, can compromise millions of records. Reports such as Cloud Insecurity highlight the devastating consequences of these missteps.
For enterprises operating in hybrid environments—where some data resides on-premises while other workloads run in the cloud—the risks multiply. Maintaining consistent database security policies across both environments is essential to prevent gaps that attackers could exploit. This means applying unified access controls, encryption standards, and monitoring practices regardless of where the database is hosted. Organizations that approach security holistically, aligning their cloud and on-premises practices, are far better positioned to defend against breaches than those treating each environment in isolation.

Database Security in the Broader Landscape
From an industry perspective, database server security should never be viewed as an isolated task but rather as part of a broader cybersecurity strategy that protects infrastructure, applications, and people. Databases are at the heart of nearly every business process, storing sensitive customer details, intellectual property, and financial data. If compromised, the impact extends far beyond the technical realm, leading to compliance violations, reputational damage, and severe operational disruption. For this reason, industry leaders increasingly treat database protection as a fundamental pillar of enterprise risk management.
Global standards and best practices frameworks have emerged to guide organizations in this area. References like Database Security highlight the importance of strong encryption for data at rest and in transit, consistent monitoring of queries and logs, and the adoption of layered defenses that make it difficult for attackers to escalate privileges. Security audits, vulnerability assessments, and penetration tests are no longer optional but essential components of ongoing protection.
As cyberattacks continue to grow in sophistication, enterprises must shift their perspective. Databases should not be seen as static repositories but as dynamic, business-critical assets requiring constant oversight and adaptive defenses. This means integrating database protection with wider initiatives, such as security awareness training, endpoint detection, and managed detection services. Ultimately, safeguarding databases ensures not only the confidentiality of information but also the resilience and continuity of business operations in the face of increasingly complex digital threats.
Conclusion
Protecting the security database on the server is critical for ensuring the confidentiality, integrity, and availability of sensitive information. By applying strong configurations, enforcing strict authentication, and implementing proactive monitoring, organizations create a first line of defense. Adding advanced strategies like behavioral analytics, encryption, and managed response capabilities provides deeper resilience against evolving threats.
Ultimately, the question of how to secure database server systems is not just technical but strategic. Databases hold the lifeblood of modern enterprises, and their protection is essential for compliance, reputation, and operational success. In an era of escalating cyber risks, database protection must remain a central pillar of every organization’s security strategy.