Netstat for Incident Response – Cybersecurity Leadership
Netstat for Incident Response
In the high-stakes world of cybersecurity incident response, every second counts. When a security breach occurs, the ability to rapidly assess the compromised system’s state, identify malicious activity, and contain the threat is paramount.
The netstat (network statistics) command-line utility, available across Windows, Linux, and macOS, is an indispensable tool for achieving this real-time visibility into network connections.
- Immediate & On-Host Visibility:
netstatruns directly on the affected system, providing an instant snapshot of active connections, listening ports, and associated processes without relying on external network monitoring tools, which might not be available or trusted during an incident. - Built-in & Ubiquitous: As a native command-line tool,
netstatdoesn’t require any installation, making it accessible even on deeply compromised systems where installing new software might be risky or impossible. - Core Network Insight: It directly exposes how a system is communicating with other devices, both internally and externally, which is the lifeblood of most malware and attacker activity (e.g., C2, data exfiltration, lateral movement).
- Forensic Value: The output of
netstatcan be logged and used as a crucial forensic artifact, demonstrating the network state of the system at various points during the incident investigation.
Essential netstat Commands and Interpretation for IR
The power of netstat lies in its command-line options. Combining these options allows for targeted investigations. Below are the most relevant commands for incident response, detailed explanations of their output, and what suspicious indicators to look for.
General Syntax: netstat [options]
1. Unveiling All Connections and Listening Ports
- Objective: To get a comprehensive view of all network activity, including established connections and open ports waiting for incoming connections. This is often the first command an IR responder runs.
- Windows Command:
netstat -ano - Linux/macOS Command:
netstat -anp(often requiressudoto see all process information)
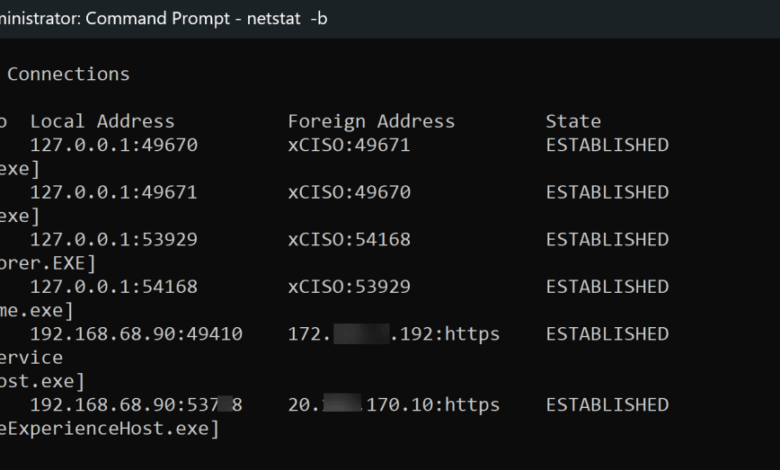
Output Explanation:
| Column | Description |
Proto |
The protocol used by the connection (e.g., TCP, UDP, TCPv6, UDPv6). |
Local Address |
The IP address of the local machine and the port number being used. 0.0.0.0:Port (IPv4) or [::]:Port (IPv6) indicates the service is listening on all available network interfaces. 127.0.0.1:Port or [::1]:Port indicates it’s listening only on the localhost (loopback interface). |
Foreign Address |
The IP address and port number of the remote computer. For listening ports, this often appears as 0.0.0.0:* or *.* (Windows) / * (Linux/macOS), meaning it’s waiting for connections from any remote address. |
State |
The state of the TCP connection. Common states include: – LISTEN: The port is open and waiting for an incoming connection. – ESTABLISHED: A connection is active and data is being exchanged. – SYN_SENT: The system has sent a SYN packet and is waiting for a SYN-ACK. – SYN_RECV: The system has received a SYN and sent a SYN-ACK, waiting for an ACK. – CLOSE_WAIT: The remote end has initiated connection termination. – TIME_WAIT: The local end has initiated connection termination and is waiting to ensure all packets are received. |
PID |
(Windows with -o, Linux with -p) The Process ID (PID) of the application or service that owns the connection or is listening on the port. This is critical for linking network activity to a specific executable. |
Program name |
(Linux with -p) The name of the execut |
Windows Example
C:> netstat -ano
Linux/macOS Example
$ sudo netstat -antp
Suspicious Indicators to Look For:
- Unknown
LISTENing Ports: Any port in aLISTENstate that is not associated with a known, legitimate service. Attackers often open high-numbered or unusual ports for backdoors or C2.- Action: Investigate the PID associated with such ports.
- Unexpected
ESTABLISHEDConnections:- Connections to unfamiliar external IP addresses, especially those outside of typical geographic regions for your organization.
- Connections to known malicious IP addresses (cross-reference with threat intelligence feeds).
- Connections on non-standard ports (e.g., port 80/443 for non-HTTP/S traffic, or port 22/3389 to unusual external IPs).
- Connections from processes that typically shouldn’t initiate external communication (e.g., system services, background utilities).
- Multiple Connections to a Single Foreign Address/Port: This can indicate C2 communication or data exfiltration.
SYN_SENTorSYN_RECVin large numbers: Can indicate port scanning attempts (incoming) or a system trying to connect to a non-existent/blocked host (outbound C2 attempts).CLOSE_WAITstates persisting for too long or in large numbers: Could indicate a process that is failing to properly close connections, potentially due to resource exhaustion or a hung malicious process.
2. Identifying the Executable (Windows Specific)
- Objective: To determine the actual program creating the network connection or listening port. This is paramount for confirming if network activity is benign or malicious.
- Windows Command:
netstat -b(often combined with-aand-nfor full context) - Note: This option can be time-consuming and requires administrative privileges.


Suspicious Indicators:
- Unknown Executable Names: If a process like
malware.exeor a strangely named executable is associated with network connections. - Legitimate Processes with Suspicious Connections: A common tactic for attackers is to inject code into or masquerade as legitimate processes (e.g.,
svchost.exe,explorer.exe). If these processes are making connections to unusual external IPs or on non-standard ports, it warrants deeper investigation.
3. Resolving Foreign Addresses to FQDNs
- Objective: To see the fully qualified domain names (FQDNs) for remote addresses, which can provide more human-readable context than raw IPs.
- Windows Command:
netstat -f - Linux/macOS Command:
netstat -f(less commonly used for this purpose on Linux, as-nis preferred for speed andlsof/ssare more powerful for resolving later).
C:> netstat -af


Suspicious Indicators:
- Malicious or Suspicious Domain Names: Domains that are known to be associated with malware, phishing, or C2 servers.
- Newly Registered Domains (NRDs): Attackers often use NRDs to host C2 infrastructure.
- Domain Generation Algorithms (DGAs): If FQDNs appear as random strings (e.g.,
kjhgfdsahgfd.com), this could indicate DGA usage by malware to evade detection.
4. Displaying Numerical Addresses (Crucial for Speed and Accuracy)
- Objective: To display IP addresses and port numbers in numerical format only, without attempting DNS lookups.
- Windows Command:
netstat -n(often combined, e.g.,netstat -ano) - Linux/macOS Command:
netstat -n(often combined, e.g.,netstat -antp)
Why it’s critical for IR:
- Speed: DNS lookups can be slow, especially on a heavily loaded or compromised system, delaying critical information.
- Evasion Bypass: Attackers might manipulate local DNS settings or use fake DNS responses to hide actual C2 IP addresses. Using
-nbypasses this, showing the true IP. - Clarity: Numerical addresses are unambiguous.


5. Real-Time Monitoring with Refresh Interval
- Objective: To observe changes in network connections over time, which can reveal transient connections (e.g., beaconing malware) or bursty C2 traffic.
- Windows Command:
netstat -ano [interval](e.g.,netstat -ano 5for updates every 5 seconds) - Linux/macOS Command:
netstat -antp [interval](e.g.,netstat -antp 5)


Combining netstat with Other IR Tools
netstat is incredibly powerful, but its true potential is unleashed when integrated into a broader IR toolkit:
- Process Investigation (
tasklist/ps):- Once
netstat -ano(Windows) ornetstat -antp(Linux) provides a suspicious PID, usetasklist /svc /fi "PID eq [PID_NUMBER]"on Windows orps aux | grep [PID_NUMBER]on Linux to get more details about the process, including its full path, parent process, and user account. This helps determine if it’s a legitimate system process or an unauthorized executable.
- Once
- Filtering Output (
findstr/grep):netstatoutput can be verbose. Usefindstr(Windows) orgrep(Linux/macOS) to filter for specific keywords, IPs, ports, or states.- Examples:
netstat -ano | findstr "ESTABLISHED"(Windows: show only established connections)netstat -ano | findstr "192.168.1.100"(Windows: show connections to a specific IP)netstat -antp | grep ":8080"(Linux: show connections involving port 8080)netstat -antp | grep "LISTEN"(Linux: show only listening ports)
- Network Capture (
Wireshark/tcpdump):- If
netstatidentifies a suspicious connection,tcpdump(Linux/macOS) or Wireshark (GUI, all platforms) can be used to capture the actual network packets for deep-packet inspection. This reveals the content of the communication, which can confirm C2, data exfiltration, or malware propagation.
- If
- Threat Intelligence Platforms:
- Take any suspicious foreign IP addresses or domain names from
netstatoutput and cross-reference them with threat intelligence databases (e.g., VirusTotal, AlienVault OTX, abuse.ch) to see if they are known malicious indicators.
- Take any suspicious foreign IP addresses or domain names from
- Forensic Imaging/Memory Analysis:
- The information gleaned from
netstatcan prioritize systems for full forensic imaging or memory acquisition, which are deeper analysis techniques.
- The information gleaned from
Limitations of netstat
While invaluable, netstat has some limitations:
- Point-in-Time Snapshot: It only shows current connections. Fast-beaconing malware might establish and close connections quickly, potentially being missed by manual
netstatchecks. Continuous monitoring or scripting is needed for this. - Obfuscation: Attackers can use techniques like process hollowing, rootkits, or kernel-level trickery to hide processes and network connections from
netstat. - Permissions: On multi-user systems, without elevated privileges (Administrator/root),
netstatmight not show all connections or associated process information. - Alternatives: Newer tools like
ss(Socket Statistics) on Linux offer more detailed and faster output for large numbers of connections, andlsof -i(List Open Files) on Linux/macOS provides more comprehensive details about processes using network sockets. Incident responders should familiarize themselves with these alternatives as well.
netstat concepts and functionality work within or alongside Binalyze AIR:
Binalyze AIR (Automated Incident Response) is a comprehensive Digital Forensics and Incident Response (DFIR) platform designed to automate and streamline the process of evidence collection and analysis across endpoints. While netstat is a manual, command-line tool, Binalyze AIR incorporates and extends the kind of network visibility that netstat provides, often in a more automated, efficient, and integrated manner.
It’s not so much that Binalyze “runs netstat” in the traditional sense for every piece of network data it collects. Instead, Binalyze automates and enhances the underlying network visibility that netstat provides, integrating it into a broader DFIR workflow:
- Automated Collection: Binalyze’s agent directly queries the operating system for active connections and listening ports, much like
netstatdoes at a low level, but then enriches this data with more process details and integrates it into its platform. - Beyond
netstat: Binalyze layers on top of this basic network visibility with features like full packet capture, network flow analysis, automated threat intel lookups, and visual timelines, providing a much richer investigative context thannetstatalone could offer. - Manual Override: The interACT feature ensures that if a manual, live
netstatquery is ever needed, it can be performed remotely and its output integrated.
In essence, Binalyze AIR aims to make the insights gained from netstat accessible, scalable, and actionable within a modern incident response framework, significantly reducing the manual effort and accelerating the detection and remediation of threats
Conclusion
netstat remains a cornerstone utility for incident responders. Its simplicity, ubiquitous availability, and direct insight into network connections make it a powerful first-response tool. By understanding its various options and knowing what suspicious patterns to look for, security professionals can quickly triage compromised systems, identify the scope of an attack, and gather critical intelligence to guide further remediation efforts. While advanced threats may require more sophisticated tools, mastering netstat is an essential skill that provides immediate and actionable insights in the critical moments of an incident
DNSChanger Malware
keywords
netstat for ir netstat for incident response tables interface statistics masquerade connections masquerade connections and multicast memberships netstat for incident response network connections routing tables interface