The Ultimate Guide to Software Supply Chain Security Risks, Threats, and Mitigations
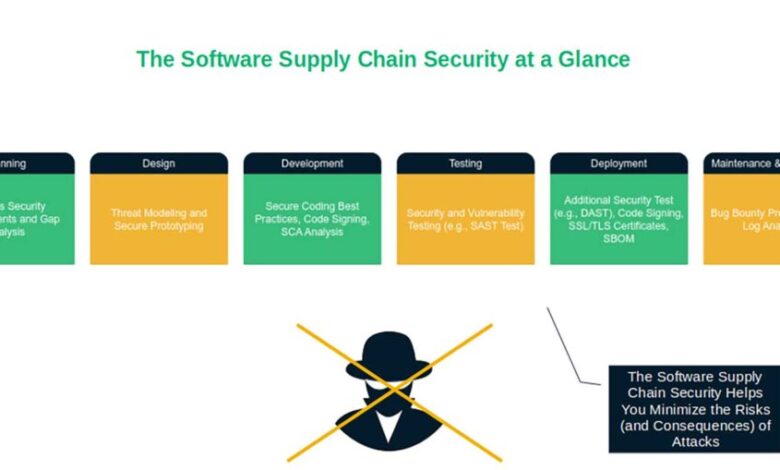
In July 2025, a core node package manager (npm) package with 28+ million downloads per week was compromised, exposing millions of projects and development environments. Discover how to enhance your software supply chain security posture to avoid a similar fate.
When was the last time your organization built an application from scratch? I bet it was a while ago. To remain competitive, software publishers must deploy code quickly. They have no time to write code bit by bit.
Enter the software supply chain, where building blocks, open-source libraries, and development tools empower businesses to prototype, develop, and release code in a flash. And if you use AI, it goes even faster.
It sounds like the perfect solution, right? So, why does the latest SecurityScorecard report say that 88% of cybersecurity leaders are concerned about software supply chain security risks? Because the software supply chain is a mixed blessing for businesses.
Software supply chain accelerates application delivery. However, the increasing complexity and reliance on open-source components, third-party services, and automated build systems introduce new vulnerabilities. Thus, every stage of the development lifecycle becomes a potential attack vector.
In this ultimate guide, you’ll learn everything you need to know about the top software supply chain risks and threats, as well as how you can mitigate them.
Software Supply Chain Security: A Definition
Software supply chain security encompasses all actions businesses take to identify, analyze, and minimize the risks involved in the development and deployment of code throughout the software development lifecycle (SDLC).
From the design phase to prototyping to its eventual release (and every stage in between), software supply chain security helps you secure every single element you use to build your application. We’re talking about everything from securing the development environments in which the software applications are built to protecting the integrity of the products themselves.
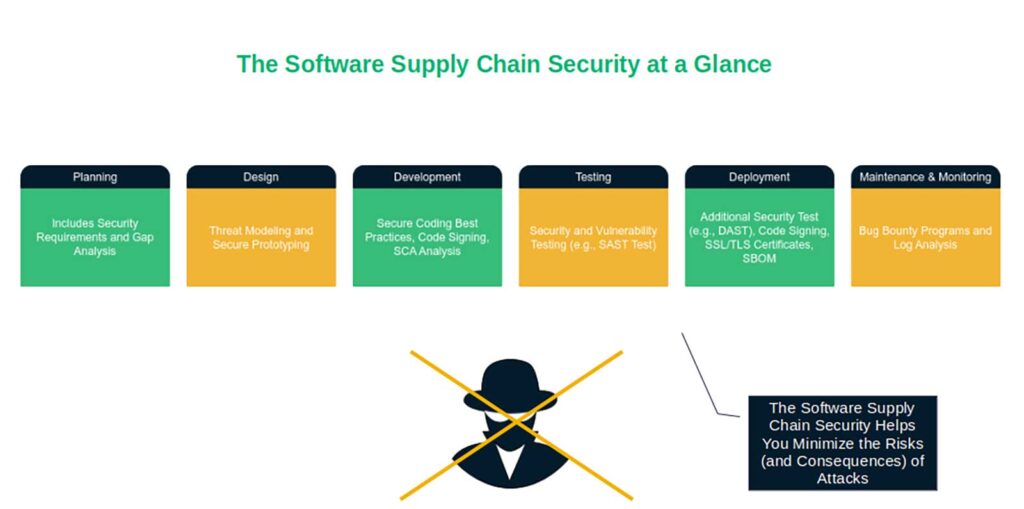
The lasting consequences of not having a secure software supply chain could impact not only your organization but also your customers and partners. Here are just a few of the ways…
5 Outcomes of Bad Software Supply Chain Security Your Organization Must Avoid
Codecov Bash Uploader, SolarWinds, and 3CX are just a few examples of the disastrous consequences that a software supply chain security failure can bring. The weakest link in your supply chain can put your whole organization, partners, and customers at risk of suffering an array of catastrophic damages.
- Data breaches. A single breach in the supply chain can have a dramatic ripple effect. In the first half of 2025, the Identity Theft Resource Center (ITRC) reports that 690 entities were victims of supply chain attacks that leaked the sensitive data of over 78 million individuals in the U.S. alone. This equates to a record-breaking surge of 11% year-over-year.
- Financial losses. Gartner predicts that the cost of supply chain attacks will reach $138 billion by 2031. OK. While your organization may not necessarily lose such a significant amount of money, you’ll still pay the consequences through fines, disrupted business operations, and cleanup efforts.
- Reputational damages. Let’s say you’ve been so unlucky that your company has been a victim of a supply chain attack. Do you know how many customers may potentially sever ties with your brand? 70% based on Vercara‘s Consumer Trust and Risk report. Rebuilding a reputation that took years of hard work and considerable investments to establish is going to take significant investments of time and effort.
- Legal liabilities. Guess who will be accountable if your customers’ sensitive data is leaked as a result of something you did (or didn’t do but should have)? You. As a result, you may have to deal with legal expenses due to angry customers or hefty fines for violating regulations such as the European Union General Data Protection Regulation (EU GDPR).
- Operational disruptions and downtime. A successful supply chain attack disrupts business operations. It may force you to delay a product release, rebuild artifacts, revoke credentials, or even take your website offline for a few days. The Kaseya attack, for instance, obliged the company and some of its clients to shut down their servers or services for days.
The list of other possible negative outcomes goes on and on. But this brings us to the question: what are some of the risks looming over every company’s horizon that lead to them? Let’s find out.
10 Common Risks and Threats to Your Common Software Supply Chain Security
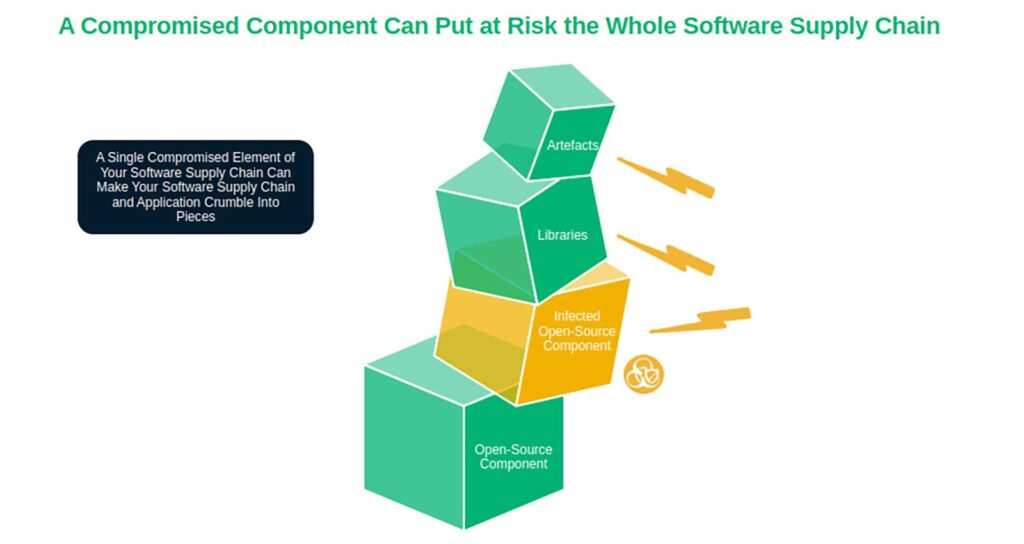
The software supply chain is a juicy target for the bad guys. This interconnection of components, libraries, plugins, repositories, and tools enables attackers to exploit a single vulnerability and trigger a massive snowball of infections and compromises.
Think about your applications like those cube towers we all played with as toddlers: they’re built with different stacking cubes, and a single vulnerable component that’s slightly out of place could take down the entire structure within seconds. The same concept applies to vulnerabilities within the software supply chain. Software applications often include open-source elements and other vulnerabilities that give cybercriminals potential vulnerabilities and supply chain entry points to exploit.
Some examples of these risks and threats include:
- Use of weak and vulnerable credentials. Solarwinds123 — that’s the weak password that enabled attackers to infiltrate SolarWinds’ not-so-secure software supply chain. Poor, default, or easy-to-guess passwords can be deduced or brute-forced. And once an attacker is in, they can wreak havoc.
- Relying on poor coding practices. Malicious actors love it when people ignore coding standards and best practices. It makes their products and systems easy to exploit. From insecurely stored API keys to hardcoding credentials, code repositories are veritable gold mines for bad guys who know what to look for. The recent GitHub CodeQL hard-coded secret that led to a supply chain attack is just one of the latest examples.
- Use of third-party dependencies. Attackers can leverage third-party software updates to inject malicious code through dependency confusion attacks. That’s exactly what happened in December 2022 when a PyTorch open-source library was compromised and used to launch a supply chain attack. The threat actors tricked applications into downloading the malicious PyTorch code instead of a legitimate update. It was done over the winter holidays when security teams are less likely to notice.
- Unrecognized (unaddressed) insider threats. Let’s go back for a moment to the SolarWinds attack. Who exposed the weak password? Likely, an employee. Yup. Sometimes employees are a company’s biggest threat. In fact, 83% of organizations reported being victims of at least one insider attack in 2024.
- Lack of security focus within your organization. Some organizations don’t prioritize security in favor of having new features and other flashy focuses. For example, Microsoft ignored a critical vulnerability for years that allowed it to be exploited in the SolarWinds attack.
- Lack of visibility. It’s easy to overlook critical vulnerabilities or non-compliant dependencies when you don’t have a clear view of all your software supply chain components. The same goes for external libraries. If you don’t assess them properly, they may introduce software supply chain security risks and flaws.
- Insufficient access controls.If you don’t limit who has access to what, or have a means of verifying only the legitimate users are accessing an account, then you’re in for a world of hurt if an employee goes rogue or their account gets compromised.
- Use of insecure third-party components and libraries’ vulnerabilities. ReversingLabs’ recent analysis shows that Python Package Index (PyPi) libraries have an average of over 149 vulnerabilities per package, while npm has 43.3 such vulnerabilities per package. So, if the code you’re developing right now includes a PyPi package, check it thoroughly before it’s too late.
- Insecure CI/CD pipelines. The continuous integration/continuous deployment (CI/CD) pipeline is another cybercriminals’ favorite target for insecure software supply chains. They can use it to introduce vulnerabilities or malicious code into the software that, once released in production, will infect anyone using the application.
- Reliance on open-source software. Black Duck’s 2025 Open Source Security and Risk Analysis (OSSRA) report shows that 97% of codebases include open-source software. Yup, open source rules for developers. However, the report also states that 86% of audited applications have open-source vulnerabilities, with 81% being high- or critical-risk vulnerabilities. So, beware. If your code also contains open-source components, it means your secure software supply chain may be at risk.
7 Ways to Secure Your Software Supply Chain
Now that you understand your enemy and the intricacies of the most common threats you face, it’s time to take action. You can implement the following to enhance your software supply chain security with effective risk and threat mitigation strategies.
1. Follow Secure Software Development Best Practices
Fast software development shouldn’t mean insecure. So, while you can’t prevent everything:
- Sign your code with a code signing certificate issued by a trusted certificate authority (CA). It’ll confirm your identity as a software publisher and protect the integrity of your code against tampering. Mandate code signing for all commits as well. It’ll authenticate the contributor and help secure your software supply chain against tampering and abuse.
- Issue and sign your software bill of materials (SBOMs). This comprehensive list of components and software dependencies will help you swiftly identify and manage your software supply chain vulnerabilities and threats. Don’t forget to request it from your software vendors as well.
- Shift security left. Embed security into every step of your software development lifecycle, from the design phase to release and monitoring. Integrate static analysis tools (SAST) early in the SDLC to scan newly written source code for vulnerabilities. Pair it with dynamic analysis tools (DAST) to seek out and fix vulnerabilities within a running application deployed in a testing environment.
- Limit access and permissions to certificates and keys. Restrict access to your cryptographic keys and certificates to only those who need said access to do their jobs (e.g., for code signing purposes). Sectigo Certificate Manager allows you to grant the appropriate level of access to the entities that need it with a click.
- Protect your backend code. Implement access control policies for the backend. For instance, you can opt for the easy-to-implement role-based access control (RBAC) to limit who can merge and deploy code. Alternatively, you can use a more granular approach via the attribute-based access control (ABAC).
2. Conduct Regular Security Risk Assessments and Update Your Response Plans
Risk assessments help you secure your software supply chain against threats and vulnerability-based attacks. Do them regularly to identify risks and prioritize how to address them. Therefore, adopt a proactive approach and develop a comprehensive strategy:
- Use software composition analysis (SCA) tools. Tools like OWASP’s Dependency-Check and Dependency-Track won’t cost you a dime. However, they can help you mitigate software supply chain security risks by mapping code dependencies, flagging vulnerabilities, and facilitating license compliance.
- Listen to the pros. Follow the guidance of SAFECOM and the National Council on Statewide Interoperability Coordinators (NCSWIC). Their quick guide is packed with valuable tips and links to other useful resources.
- Hope for the best but prepare for the worst. Prepare incident response, business continuity, and disaster recovery plans in case of a software supply chain security attack. There are several frameworks that you can look to for inspiration. The National Institute of Standards and Technology (NIST) SP 800-61, for example, offers detailed guidance and recommendations applicable to organizations of any size.
3. Protect Your Credentials, Systems, and Network
In June 2025, Cybernews researchers discovered a collection of a staggering 16 billion stolen credentials that may have led to one or more massive software supply chain security incidents. So, protect your usernames and passwords:
- Go beyond the traditional user ID and password. Implement multi-factor authentication (MFA) or go passwordless using a personal authentication client certificate (i.e., certificate-based authentication) purchased from a trusted source like SectigoStore.com whenever possible.
- Strictly control access to your network and systems. Your HR guy doesn’t need access to your SDLC or development-specific applications and databases. Nor do your partners and vendors, in most cases. Implement the principle of least privilege at all times. This way, everyone has access only to the tools and systems they need to do their jobs.
- Store your passwords safely. Never save passwords. It doesn’t matter if they are in plaintext or encrypted. Take the habit of storing only the salted password hash values in your databases. This way, if an attacker breaks into it, they will be left with a list of unusable gibberish in lieu of your sensitive data.
4. Implement Continuous Monitoring and Logging Throughout the SDLC
Secure your software supply chain by adding another layer of protection through continuous monitoring and logging, even after deployment.
- Use supply chain risk management software (SCRMS). These tools offer several features like risk assessment and analysis, threat intelligence, compliance management, and vendor risk management. It empowers you to continuously monitor your supply chain security posture, alerting you to anomalies and suspicious activity.
- Monitor your certificates and keys through a single platform. We get it —not all organizations have the skills, time, and resources to keep on top of everything. Software like Sectigo Certificate Manager takes the burden off your staff by automating certificate management, monitoring, and logging in one go.
- Track and log everything you can. Record which users and systems have access to what, their activities, and the changes they make. (This includes code repository modifications.) It’ll enable you to quickly identify anomalies, lock suspicious accounts, and set up automatic alerts.
- Automate log analysis. Integrate application detection and response (ADR) solutions early in the software development lifecycle. These multilayered detection tools analyze logs using advanced threat intelligence techniques to identify anomalies in real-time and automate mitigation response.
- Monitor repositories. Tools like GitHub Audit Log and GitLab Activity Feed can help you detect sudden privilege escalations or unauthorized access attempts in a flash.
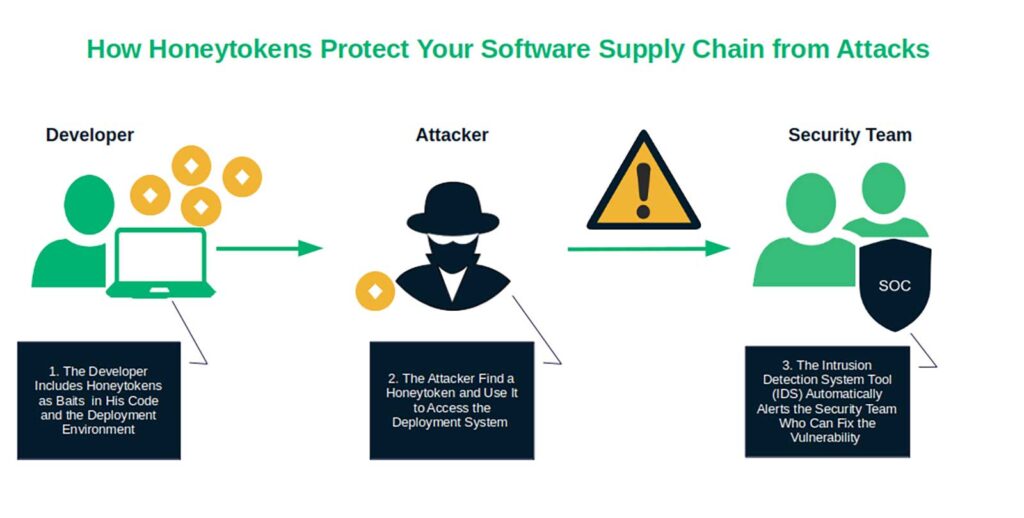
- Deploy intrusion detection system tools (IDS). Besides monitoring and analyzing network traffic, open-source tools like Suricata and Snort utilize honeytokens (i.e., phony secrets in your legitimate systems) to lure threat actors. (These differ from honeypots, which are decoy systems.) So, when an attacker accesses your SDLC or CI/CD pipeline using the honeytoken, the security team is automatically alerted. Isn’t that great? Now they can patch any potential weakness before it’s used against you.
5. Utilize Risk Management Frameworks
Software supply chain security frameworks are fundamental tools to help you assess your risks and evaluate mitigation priorities. Get familiar with key frameworks for supply chain security and pick the one that best fits your needs.
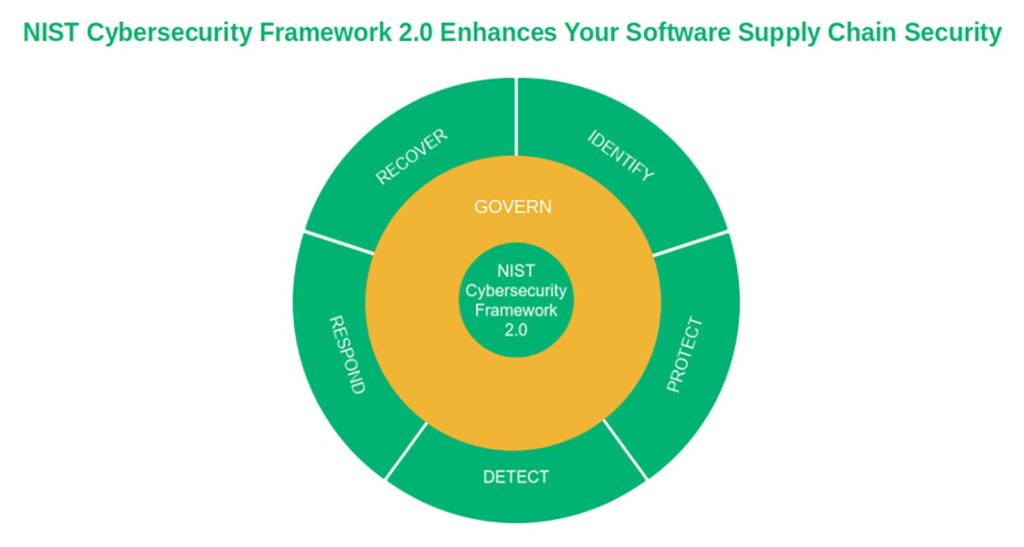
The NIST Cybersecurity Framework
The NIST Cybersecurity Framework 2.0 lists six key points that help reduce software supply chain security risks, even if you’re a small business.
The ISO/IEC 27001
Even if the ISO/IEC 27001 is a standard for information security management systems, it also includes best practices to enhance the security of the information exchanged between organizations and suppliers, such as vendor vetting, contractual requirements (e.g., SBOMs, secure SDLC), and monitoring.
The Open Software Supply Chain Attack Reference (OSC&R)
This comprehensive open source framework is based on the renowned MITRE ATT&CK framework. It was specifically designed by experts who work (or worked) for companies like Google, GitLab, and Check Point Software Technologies to detect, prevent, and mitigate supply chain attacks.
By implementing this software supply chain security framework, you’ll get a hacker-centric view. It won’t give you access to attackers’ deepest secrets, but it’ll help you understand how they see and target the supply chain.
6. Keep Your Software Up to Date and Implement Vulnerability and Patch Management
Who can forget the 2017 Equifax data breach? It affected over 147 million customers and cost the company a fortune in direct and indirect costs. The root cause? An unpatched vulnerability. An outdated or unpatched software is a disaster waiting to happen.
- Know your vulnerabilities. The bad guys know them all; you should, too. Identify, prioritize, and patch known vulnerabilities throughout the building process to prevent them from becoming an issue. Don’t forget to test them first.
- Monitor and update dependencies. Put your SBOM to good use and transform it into a dynamic force. GitLab for example, allows you to integrate any SBOM into your SecDevOps workflow and connect it with SAST and DAST tools. This way, dependencies are continuously analyzed for vulnerabilities and developers alerted, so attackers won’t be able to exploit them.
- Be careful with automated updates. Never fully automate patch management and updates. While it can be convenient, it can also have dire consequences. Opt for a managed automated update process (e.g., incremental updates). This way, if something goes wrong, you’ll still be in control.
7. Educate and Regularly Test Your Teams
The latest Verizon report confirms that the most widespread link in data breaches is us: the human element. That’s right. You can have the best processes and frameworks in place, but if your security teams and general employees aren’t on board, then attackers will still prevail.
To secure your software supply chain effectively, everyone must be informed and know their role in your software supply chain security (and overall cybersecurity defenses). This means you must:
- Train your employees. Educate your staff about how to recognize, respond to and report internal and external threats. Ensure they’re familiar with security processes and best practices and, above all, that they put them into practice. This holds true for both your security and general employees (although the different employee groups will require different types and levels of training).
- Keep them involved. Nudge them to regularly check threat intelligence and vulnerability databases such as the common vulnerabilities and exposures (CVE) database and vendors’ website security bulletins. Allow them to participate in communities and forums to stay informed about emerging threats and best practices. For your less technical roles, keep those employees in the loop about common threats and vulnerabilities with information about what to look out for.
- Ensure they understand and comply with privacy and security regulations. Educate them on relevant standards and privacy, and security laws and regulations that could impact your software supply chain security (e.g., GDPR). Show them the harsh consequences of non-compliance (e.g., financial losses, poor reputation, and operational disruptions).
- Test your staff’s knowledge. Educating your staff is only the first step toward software supply chain security. Check their understanding by conducting internal software supply chain attack simulations as suggested by top industry experts. It’ll be fun and, at the same time, it’ll harden your security culture and minimize risks.
Interested in learning more about how to enhance your software supply chain security? Check out the full list of NIST Cybersecurity Supply Chain Management publications and OWASP’s software supply chain security cheat sheet.
Final Thoughts About the Ultimate Guide to Software Supply Chain Security Risks, Threats, and Mitigations
We get it — that’s a lot to digest in one go. Nevertheless, the risks are real, and with AI-powered attacks, they’re poised to increase. So, start with the basics, sign your codes and SBOMs, secure your network with SSL/TLS certificates, train your teams, and go from there.
Be proactive, and you’ll soon see that after establishing robust security practices, fostering a culture of security awareness, and leveraging modern tools and frameworks, you’ll have significantly reduced your exposure to software supply chain security threats and protected your assets and customers.



