What is Attack Surface Management? Tools and Best Practices
Attack surface management (ASM) is a fundamental cybersecurity approach that involves continuously identifying, analyzing, remediating, and monitoring all the current and potential ways an outside attacker might try to break into your organization’s systems. These entry points are collectively known as your organization’s attack surface.
Every business leaves digital footprints. Some are deliberate and well-documented, like cloud applications, websites, domains, and external integrations. Others are like faint or forgotten tracks that reemerge unexpectedly: test environments left open to the public, untracked SaaS and AI services spun up without IT approval, or leaked credentials and sensitive data surfacing on dark web forums.
Today’s attack surfaces are no longer confined to an organization’s data center. Shaped heavily by remote work and external partnerships, the average modern attack surface now contains attack vectors that stretch across the internet. These scattered footprints are fertile ground for attackers hunting hidden vulnerabilities.
This is where attack surface management steps in. ASM gives security teams the tools needed to secure every corner of their attack surface before attackers can strike. For businesses navigating complex ecosystems, ASM is a frontline defense against data breaches, reputational damage, and regulatory fallout.
Understanding Your Attack Surface Components
Your attack surface is all the hardware, software, SaaS, and cloud assets that are accessible across the Internet and that process or store your data. Think of it as the total set of attack vectors cybercriminals could exploit to breach your systems or extract sensitive information.
Your organization’s attack surface is made up of:
- Known assets: Inventoried and managed assets such as your corporate website, servers, and the dependencies running on them
- Unknown assets: Such as Shadow IT or orphaned IT infrastructure that was stood up outside of the purview of your security team, such as forgotten development websites or marketing sites
- Rogue assets: Malicious infrastructure spun up by threat actors or hackers, such as malware, typosquatted domains, or a website or mobile app that impersonates your domain.
- Vendors: Your attack surface doesn’t stop with your organization. Third-party vendors introduce significant third-party risk. Even small vendors can lead to large data breaches, just like the HVAC vendor that eventually led to Target’s exposure of credit card and personal data on more than 110 million consumers.
Millions of these assets appear online daily and are entirely outside the scope of traditional perimeter security tools like firewalls and endpoint protection services. This external exposure is sometimes referred to as your external attack surface and digital attack surface.
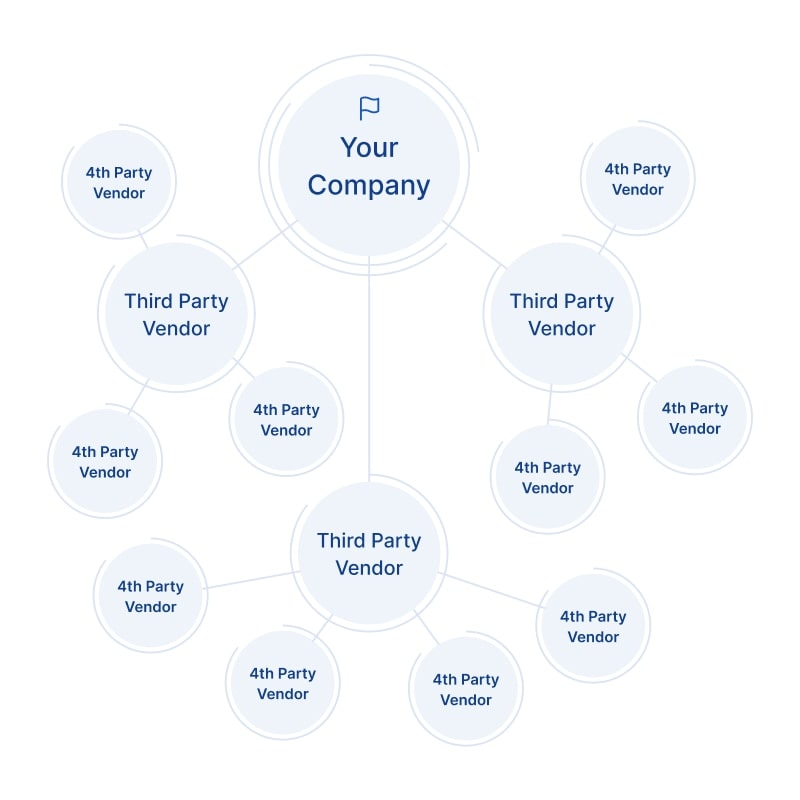
Your attack surface also encompasses all fourth-party suppliers (your suppliers’ suppliers) and nth-party suppliers(your fourth-party suppliers’ suppliers and so on down the chain). Each of these supplier ecosystems can introduce additional risk vectors.
Why Attack Surface Management Matters in Modern Cybersecurity
Every new digital initative your organization takes adds another layer to your attack surface. These layers bring opportunity, for you and for cybercriminals as they also create more places for vulnerabilities to hide. Attackers increasingly focus on what’s publicly visible, knowing that a single overlooked asset or misconfiguration can become the entry point they need to carry out a data breach.
ASM is a critical cybersecurity defense because it helps organizations prevent and mitigate cyber risks arising from a wide range of factors, including:
- Legacy systems, IoT, and shadow IT assets that might be forgotten or poorly secured
- Human mistakes and omissions, such as phishing-related exposures and accidental data leaks
- Vulnerable and outdated software that attackers can exploit before patches are applied
- Unknown open-source software (OSS) dependencies introduced through development pipelines
- AI risk, such as open or exposed ports and data leakage
- Large-scale attacks targeting entire industries or sectors
- Targeted cyber attacks focused specifically on your organization or brand
- Intellectual property infringement, such as unauthorized use of brand domains or assets
- IT inherited from mergers and acquisitions, where visibility gaps often exist
- Vendor-managed assets that extend your risk perimeter beyond your direct control
Threat intelligence is all about timely identification. It’s the difference between caching exposures before they’re exploited and learning about them after attackers have breached your environment. Remember, all it takes is one vulnerable point or security gap in your organization or broader IT ecosystem to compromise your entire business.
Without ASM, security teams operate in the dark and are stuck reacting to incidents instead of preventing them. For modern cybersecurity programs, complete attack surface visibility is no longer optional. It’s the first step toward controlling digital risk and proving resilience.
How to Build an Effective Attack Surface Management Program
At its core, an effective attack surface management program follows a simple, yet continuous lifecycle: identify assets, understand the risks associated with these assets, eliminate these risks, and continuously monitor for new assets and emerging vulnerabilities.
While on paper these principles seem straightforward, turning this lifecycle into a bulletproof security practice requires clear steps, the right tools, and ongoing commitment across an organization.
Here’s a simplified, step-by-step roadmap you can follow to build a strong ASM program:
1. Asset discovery and inventory
The first step in ASM is knowing what assets your organization owns and which are exposed to the internet. This means identifying and organizing all publicly-facing assets connected to your organization, including known systems, domains, subdomains, web applications, APIs, cloud storage, network devices, email servers, and public code repositories. Without this comprehensive visibility, managing ASM risk effectively and creating a thorough ASM program isn’t possible.
Best practices for asset discovery
- Automate for consistency and scale: Automation ensures asset discovery happens consistently and without gaps, reducing human error. It allows your team to track thousands of assets, even as new services or domains appear daily.
- Combine diverse data sources: Effective discovery blends multiple external signals: DNS sweeps, certificate transparency logs, WHOIS lookups, and internet-wide scans. Using varied data sources increases your chances of detecting hidden assets or shadow IT.
- Integrate asset discovery with ownership and context: Don’t just build lists. Map assets back to business units, vendors, and critical systems. This context helps security teams prioritize risks and identify the right owners for remediation.
- Make discovery part of daily operations: Asset discovery should run continuously and feed directly into security tools and workflows. Treat it as an ongoing security discipline, not a periodic project.
2. Attack surface reduction
The second step is knowing that not every exposed asset needs to remain online. Attack surface reduction involves minimizing your organization’s digital footprint by eliminating unnecessary services, closing unused ports, and taking down domains and other assets that no longer serve a purpose. The smaller your organization’s attack surface is, the fewer opportunities attackers will have to exploit it.
Best practices for attack surface reduction
- Monitor DNS and certificates: Track new domain registrations, lookalike domains that could be used for phishing or brand impersonation, and expiring SSL/TLS certificates. Attackers often try to exploit these gaps for brand abuse and man-in-the-middle attacks.
- Maintain patch and configuration management: Many breaches stem from known vulnerabilities or systems left in default configurations. Establish disciplined processes for patching, installing software updates, and hardening configurations, especially across all internet-facing assets.
- Review employee access regularly: Excessive permissions and shadow IT expand your organization’s attack surface. Periodically review user access and install IAM best practices to ensure employees have only the permissions they truly need, and remove dormant accounts or unused credentials.
- Integrate ASM into zero-trust and DevSecOps workflows: Security is most effective when built into how technology is developed and deployed. Feed ASM insights into DevSecOps pipelines to catch risks early, and align attack surface management practices with zero-trust principles to reduce lateral movement.
3. Analyze risk and prioritize what matters most
Once you have identified all of your organization’s assets and determined where they are exposed, the next step is to figure out which risks are the most critical. Take the time to analyze each vulnerability or misconfiguration to determine where attackers are most likely to strike. Use business context and predict what would cause the most harm to put yourself in the shoes of the attacker.
Best practices for analyzing attack surface risk
- Correlate exposure with known vulnerabilities: Link discovered assets to vulnerability databases and threat intelligence feeds to identify known flaws that attackers could exploit.
- Consider business impact, not just technical severity: A vulnerability on a public marketing site might carry far less risk than the same vulnerability on a production system containing sensitive data. Weigh technical findings against business context.
- Identify high-value and high-risk assets: Classify assets based on their sensitivity, criticality, potential business impact if compromised, and how easily attackers could reach them from the internet. Assets exposed directly online generally carry a higher risk than those protected behind authentication or VPNs.
- Use risk scoring and prioritization Tools: Leverage tools that assign risk scores to vulnerabilities or assets to help prioritize limited resources toward fixing the most dangerous exposures first.
4. Attack surface remediation
Now that you’ve identified and analyzed your organization’s most pressing ASM risks, it’s time to fix them. Attack surface remediation can involve a variety of processes, from patching software, reconfiguring systems, removing sensitive data from public exposure, updating credentials, or taking down malicious domains. Coordination across teams and departments is key.
Best practices for attack surface remediation
- Develop clear remediation workflows: Define processes for triaging, assigning, and tracking remediation tasks across security, IT, and development teams.
- Assign ownership and communicate priorities: Ensure specific teams are accountable for fixing issues and understand the business impact and urgency behind each task.
- Track progress and verify fixes: Monitor all remediation efforts closely, confirm vulnerabilities are fully resolved, and maintain documentation and metrics to demonstrate risk reduction.
- Align remediation timelines with risk: All risks are not created equal. Set realistic deadlines based on the severity and potential business impact of each vulnerability to prioritize effectively.
5. Continuous attack surface management
Traditional ASM and asset discovery often capture a static snapshot of an organization’s systems. However, as we previously discussed, an organization’s digital environment rapidly evolves as new assets appear, configurations shift, and vendors update their infrastructure. Continuous attack surface management goes beyond simple asset lists by providing real-time visibility and detecting new exposures as soon as they emerge. This proactive shift helps modern security teams stay ahead of attackers who are getting wiser every day.
Best practices for continuous ASM
- Align people and processes: Define clear roles and responsibilities for responding to new asset alerts, managing risk scoring, and triaging changes across IT, security, and DevOps teams.
- Integrate with broader security workflows: Feed continuous ASM insights into SIEMs, SOAR platforms, incident response processes, and DevSecOps pipelines to ensure issues are addressed quickly and not siloed.
- Measure and improve over time: Track key metrics, such as how quickly new assets are identified or misconfigurations are resolved, and analyze trends to demonstrate progress and secure future investment.
- Maintain historical context and stay adaptive: Keep a record of how your attack surface evolves over time to identify patterns, investigate incidents, and adapt your ASM program as business needs, technologies, and threats change.
Top Attack Surface Management Challenges
Developing an effective attack surface management program is challenging because modern attack surfaces are growing faster than most security teams can track. Even with strong processes and talented professionals in place, many organizations face significant challenges in maintaining visibility and reducing risk:
- Shadow IT, shadow AI, and untracked SaaS: Gartner predicts that by 2027, 75% of employees will be using technology outside their IT team’s approval. This widespread adoption is a serious security concern for ASM teams, as these shadow systems often handle sensitive data but remain invisible to traditional asset inventories and perimeter security tools.
- Difficulty managing rapidly scaling asset inventories: The average security team manages around 165,000 digital assets. An organization’s digital ecosystem is constantly evolving. Domains are registered. New services go live. Vendors change infrastructure. These rapid transformations quickly outpace manual inventories, creating outdated processes and significant gaps that attackers are waiting to exploit.
- Limited context about discovered assets: Even when new assets are detected, security teams often struggle to understand ownership, business impact, or technical details quickly enough to prioritize remediation. 43% of businesses report they spend more than 80 hours a week on asset discovery.
- Emerging threats on the deep and dark web: Most security teams are only equipped with tools to monitor the open internet. However, outdated credentials, sensitive data, and brand references routinely appear on forums and marketplaces beyond the public internet. Detecting and responding to these exposures requires specialized dark and deep web monitoring.
Overcoming these difficult challenges requires continuous visibility across the open, deep, and dark web, as well as a systematic process for asset discovery and proactive incident response. These needs have led many organizations to deploy modern attack surface management solutions.
Key Components of a Robust Attack Surface Management Solution
Modern attack surfaces are sprawling, fast-moving, and increasingly difficult to secure with traditional tools alone. A robust attack surface management solution needs to go beyond simple asset discovery. It must combine deep visibility, actionable threat intelligence, and streamlined security operations so security teams can stay ahead of attackers, not merely react to them.
Below are the three essential pillars of any strong ASM solution and the capabilities you should look for.
Attack surface visibility
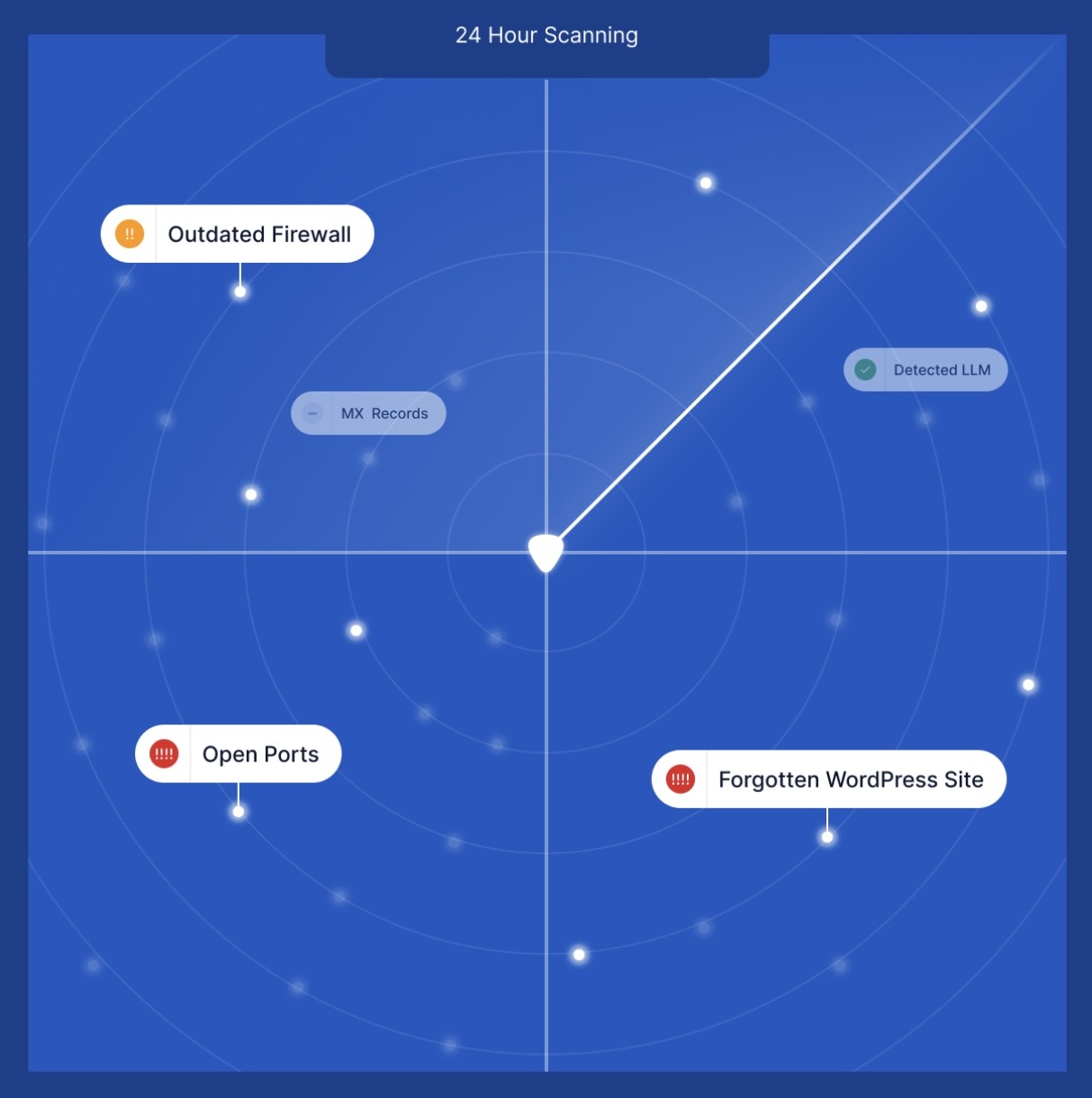
You can’t secure what you can’t see. Unknown or forgotten assets, like shadow IT, abandoned domains, or misconfigured services, create blind spots that attackers actively seek out.
A modern ASM solution should help you expose what attackers target and reduce your risk with the following capabilities:
- Continuous asset discovery and inventory: Detect both known and unknown internet-facing assets, including domains, IPs, subdomains, cloud resources, APIs, and more, with daily scans for up-to-date coverage.
- Attack surface mapping: Visualize your entire external infrastructure, helping you quickly identify gaps, overlaps, and potential security weaknesses.
- Misconfiguration and open port detection: Find exposed services, default configurations, and unnecessary open ports before attackers can exploit them.
- Vulnerability monitoring and prioritization: Automatically correlate discovered assets with real-world vulnerability data (CVEs, KEV, EPSS) to surface the most critical exposures.
Why attack surface visibility matters: Unknown exposures and unmonitored assets are a leading cause of breaches and compliance failures. Visibility is the foundation for managing cyber risk effectively.
Learn more about UpGuard Breach Risk’s attack surface visibility features.
Threat intelligence
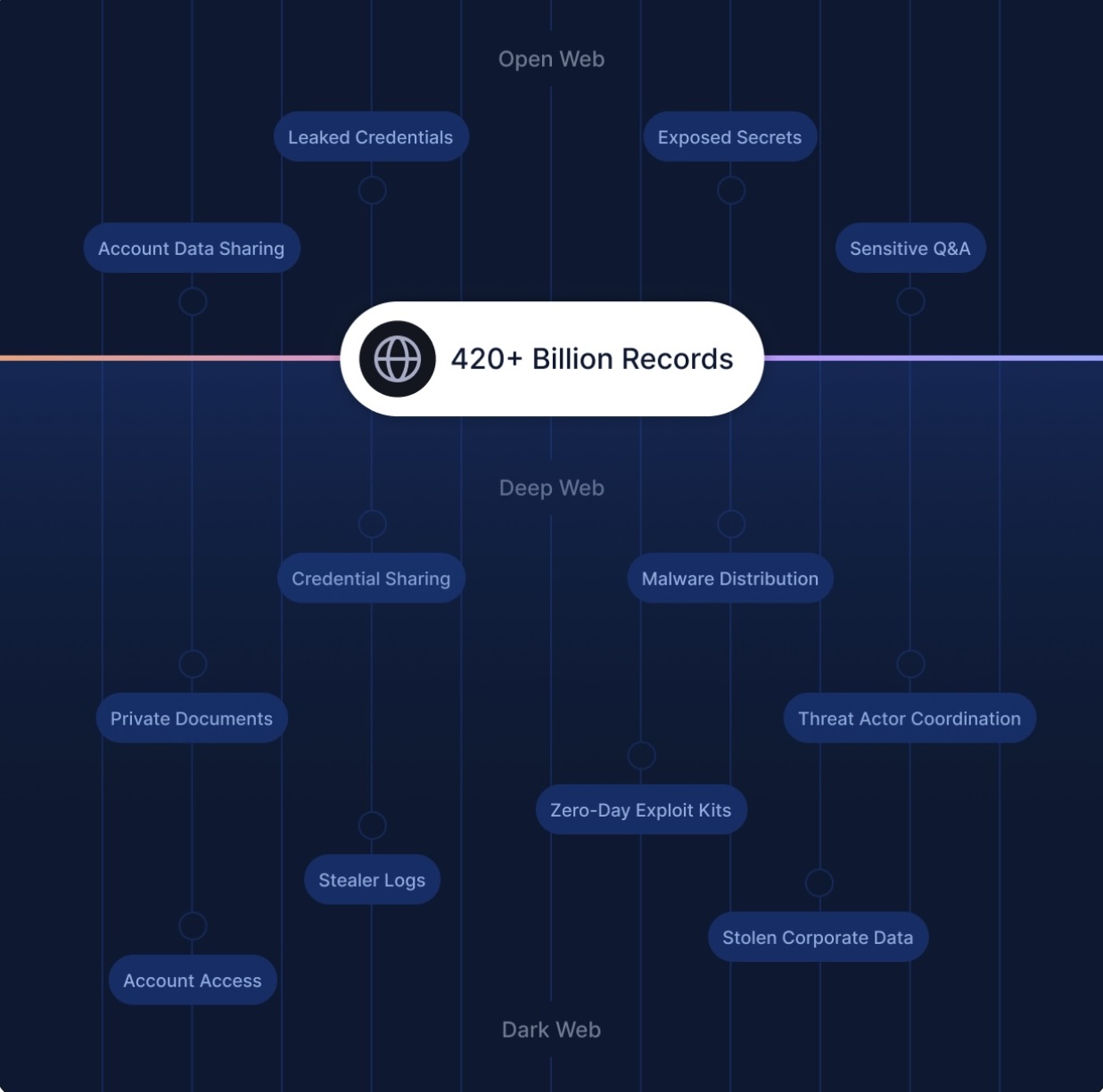
Uncover threat signals before they’re weaponized.
Attackers don’t just probe your infrastructure. They plan, coordinate, and discuss potential targets across the open, deep, and dark web. A strong ASM solution integrates threat intelligence capabilities to detect emerging threats before they hit your network:
- Threat monitoring across open, deep, and dark Web: Scan ransomware leak sites, dark web forums, infostealer logs, public breach dumps, and code repositories to detect leaked credentials, sensitive data, and brand impersonation risks.
- AI-powered threat triage: Act as a virtual analyst, filtering noise, clustering related indicators, and highlighting credible threats that require immediate action.
- Typosquatting and impersonation detection: Identify malicious or lookalike domains that attackers use for phishing, fraud, or brand abuse campaigns.
- Leaked credential monitoring: Track corporate credentials appearing in breach data or dark web marketplaces and correlate them to specific domains or executive accounts.
- Multi-source signal correlation: Aggregate intelligence from diverse channels, including malware logs, chat site chatter, and developer platforms, for contextual insights into how your organization is being targeted.
Why threat intelligence matters: Cybercriminals often act in secrecy, selling or discussing stolen data before launching attacks. Early intelligence shortens response times and helps prevent breaches.
Learn more about UpGuard Breach Risk’s threat intelligence features.
Streamlined security operations

Security teams are stretched thin. Without automation and clear processes, even the best insights can become overwhelming. A robust ASM solution empowers efficient operations through:
- Alert prioritization and risk scoring: Separate critical threats from background noise using risk scoring models based on real-world exploitability and business impact.
- Remediation workflows and playbooks: Provide guided steps for fixing vulnerabilities, automate ticket creation, and streamline hand-offs between security, IT, and development teams.
- Security profiles, benchmarking, and compliance reporting: Generate tailored reports for regulatory frameworks (DORA, CPS 230, SEC Cyber Rules), cyber insurance, and executive summaries, helping prove security posture and risk reduction.
- Native integrations and automation: Connect seamlessly with tools like Slack, Jira, Zapier, and SIEM/SOAR systems to embed ASM into broader security workflows.
- Asset portfolios and subsidiaries: Enable organizations to organize assets by region, business unit, or subsidiary, ensuring the right teams have ownership and visibility.
Why streamlined operations matter: Security leaders need to move fast, reduce manual workloads, and demonstrate control to executives, boards, and regulators. Streamlining operations turns ASM insights into real-world protection.
Learn more about UpGuard’s automated reporting workflows.
A modern ASM platform brings these three pillars together, empowering security teams to see their entire attack surface, detect emerging threats, and act quickly to reduce risk. As attackers have grown more sophisticated, dedicated ASM solutions have become a strategic necessity for cyber resilience.
Why UpGuard for Attack Surface Management
Modern attack surface management is complex, but it doesn’t have to be overwhelming. UpGuard Breach Risk is designed to help organizations stay ahead of threats by combining comprehensive visibility and automated asset discovery with practical risk reduction workflows and historical tracking.
UpGuard’s ASM capabilities help security teams:
- Continuously discover internet-facing assets
- Monitor for emerging risks on the deep and dark web
- Classify and organize assets for better context
- Prioritize risks with data-driven scoring
- Track changes over time
- Integrate with existing workflows
“UpGuard is a very handy tool for monitoring our attack surface and effectively categorizing potential attacks based on severity. The automated reports by UpGuard helped us swiftly identify and respond to threats, enabling us to safeguard our systems. Additionally, UpGuard also helps us figure out the health of any vendor tool we integrate.”
– Sanjay Singh, Director of DevSecOps and IT, Games 24×7
UpGuard Breach Risk platform transforms attack surface management from a periodic checklist into a proactive, continuous practice, helping organizations protect their data, brand, and customers in an increasingly digital world.