What it Means (and Doesn’t Mean) for Data-Centric Security
The cybersecurity industry witnessed a seismic shift last week with Palo Alto Networks’ $25 billion acquisition of CyberArk. This landmark deal represents both a dramatic departure from Palo Alto’s historical M&A playbook and a logical progression in their strategic vision.
Let’s unpack what this means for the evolving data security landscape—and what critical piece is still missing from the puzzle.
A Bold New Direction That Was Hiding in Plain Sight
At first glance, this acquisition appears to break with Palo Alto Networks’ established pattern in two significant ways:
- Unprecedented Scale: At $25 billion, this represents Palo Alto’s largest acquisition by far, signaling a high-stakes bet on identity security as a cornerstone of their future strategy.
- Category Expansion: By moving decisively into the identity and privileged access management (PAM) space, Palo Alto is venturing beyond their traditional network security stronghold.
Yet, upon closer examination, this move was almost inevitable. CEO Nikesh Arora has consistently emphasized the “platformization” of cybersecurity—the strategic consolidation of security capabilities into comprehensive platforms that address the full spectrum of enterprise needs. This philosophy has guided Palo Alto’s transformation from a firewall company into a multi-platform security provider.
“Our market entry strategy has always been to enter categories at their inflection point, and we believe that moment for Identity Security is now,” Arora’s statement reads.
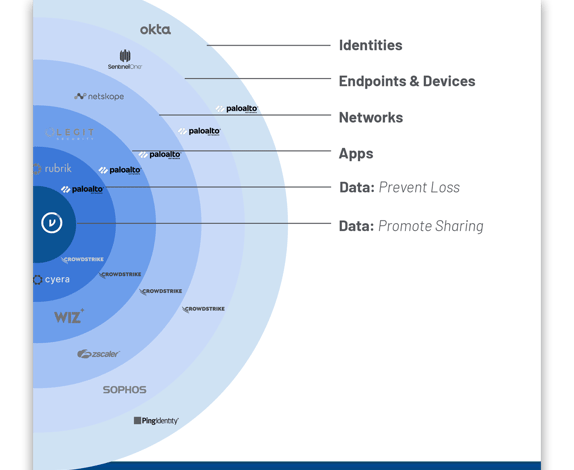
The signs were clearly visible in December 2023 when Palo Alto “shifted left” on the data control plane by acquiring Dig Security, entering the Data Security Posture Management (DSPM) space. This move strengthened their capabilities in preventing data loss by providing visibility into where sensitive data resides and identifying vulnerabilities.
With CyberArk, they’ve now “shifted right” into identity access management, privileged account security, and identity governance. This represents one of the final pieces in Palo Alto’s mission to consolidate the zero trust control plane, creating a comprehensive security framework that spans networks, endpoints, applications, identities, and data.
Data Sharing = Core of Zero Trust Control Plane/blog%20-%20CyberArk%20and%20Palo%20Alto/Control%20Plane%20Update%20PAN%20+%20CyberArk_FINAL.png?width=574&height=548&name=Control%20Plane%20Update%20PAN%20+%20CyberArk_FINAL.png)
The Missing Piece: Data Grip for Secure Sharing and Collaboration
While the Palo Alto-CyberArk combination creates a formidable security platform that addresses many aspects of the zero trust architecture, there remains a critical capability gap that neither company addresses: enabling organizations to maintain control of sensitive data once it’s shared outside their perimeter.
At Virtru, we call this capability “data grip”—the ability to apply and enforce granular policies and access controls on sensitive data as it moves beyond organizational boundaries through emails, files, and collaborative workflows.
Data grip exists at the intersection of data that has been tagged with attributes, and identities (human and machine) that have been authenticated with entitlements and need-to-know. This intersection is precisely where Virtru excels, providing organizations with persistent control of their data wherever it travels.
Recommended Reading: What is Data-Centric Security?
The Power of TDF: Open Standards for Data-Centric Security
The foundation of Virtru’s data grip capability is the Trusted Data Format (TDF), an open standard invented by Virtru co-founder Will Ackerly. TDF enables persistent protection and granular policy enforcement throughout the data lifecycle, regardless of where that data travels or how it’s shared.
Unlike traditional security approaches that focus on protecting networks, devices, or applications, TDF wraps each piece of data in its own security envelope. This means the protection stays with the data itself, ensuring that access controls, encryption, and policies remain enforced even when data is shared with external partners, stored in third-party systems, or accessed from unmanaged devices.
Recommended Reading: What is the Trusted Data Format (TDF), And How Does It Work?
Why Data Grip Matters in a Zero Trust World
Data sharing is not optional—it’s essential. Organizations must collaborate with partners, share information with customers, and enable data-driven innovation to remain competitive. Yet they must do so while maintaining control and compliance.
This is why data grip is so crucial. It allows organizations to:
- Share confidently: Exchange sensitive information with partners, customers, and vendors without losing control
- Innovate securely: Leverage data for new initiatives and collaborative projects while managing risk
- Create value: Unlock the full potential of data assets through secure sharing and collaboration
- Maintain control: Revoke access, set expiration dates, and track usage even after data has left your environment
The Palo Alto-CyberArk combination strengthens several pillars of the Zero Trust architecture, including user identity, device security, application protection, and data visibility. However, it’s Virtru’s TDF-powered platform that completes the data security control plane by enabling secure data sharing and collaboration beyond organizational boundaries.
Looking Ahead: The Future of Data-Centric Security
As enterprises continue their digital transformation journeys, the ability to share data with others, while maintaining grip, will be a foundational component of every zero trust security strategy.
The Palo Alto-CyberArk acquisition signals a broader industry recognition that security must be identity-aware and data-centric. At Virtru, we’ve been championing this approach for years, and we’re encouraged to see the market moving in this direction.
However, true data-centric security requires more than just knowing where your data is and who has access to it—it demands the ability to maintain control of that data throughout its entire lifecycle, even as it travels outside your walls. This is the promise of data grip, and it represents the next frontier in the evolution of zero trust security.
As organizations assess their security strategies in light of this industry-shaking acquisition, they would be wise to consider not just how they’ll protect data within their environments, but how they’ll maintain control of it everywhere it goes.
That’s where Virtru and TDF come in, completing the zero trust control plane with the critical capability of persistent, policy-based protection for shared data.



